Cyber espionage group ‘Strontium Stealer’ has launched a Remote Access Trojan (RAT) ‘LithiumRAT’ packed with new features to enhance malware attacks and gain full administrative privileges.
Earlier in April, the group had conducted a poll on the dark web, seeking inputs from users about what features they wanted in the Remote Access Trojan (RAT) that they were building.
The options included functions such as taking “screenshots of the target’s webcam” and “Live streaming the target’s webcam”.
From Strontium Stealer to the launch of LithiumRAT – How it all began
Strontium, operating from Russia, gained notoriety in 2020 through a Microsoft report about their stealer activities targeting Office365.
The information stealer was aimed at organizations belonging to the United States of America and the United Kingdom, involved in political elections. The group managed to compromise more than 200 organizations between September 2019 and June 2020.
The group targeted several high-profile entities.
“It was also identified in the Mueller report as the organization primary responsible for the attacks on the Democratic presidential campaign in 2016,” a Microsoft blog read. They gained access through spear phishing emails.
FusionCore’s use of Strontium stealer

FusionCore, the cybercriminal group from Europe, found an effective information-stealing tool in the Strontium Stealer.
Besides, Strontium, the group that was founded in 2022 by a member called Hydra relied on Typhon Reborn stealer, NoMercy, infostealer, RootFinder Stealer, Cryptonic Crypter, RootFinder ransomware, SarinLocker, and many others.

The group created a special support page for Strontium stealer to seek reviews and feedback from hackers and fellow members to build a more capable information stealer.
“The server and client components of the malware are lightweight. The client component is only 83KB in size. The malware is designed to bypass majority of anti-virus programs,” a CYFIRMA report read.
Launching the new LithiumRAT
A Threat Analyst going by the name of RussianPanda tweeted about the launch of the final version of the Strontium Stealer RAT, the LithiumRAT with the following screenshot with its features –
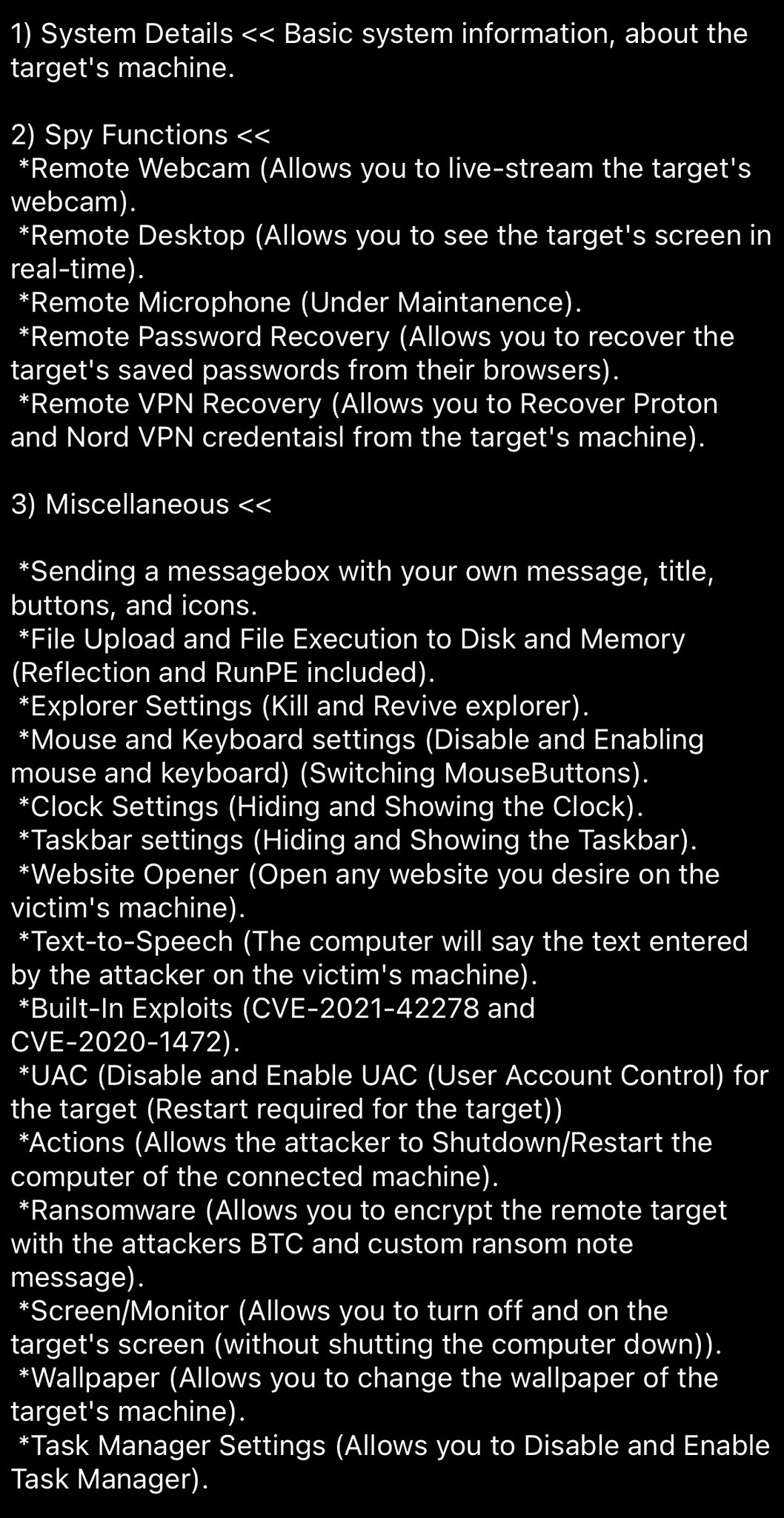
The Strontium Stealer’s LithiumRAT can steal data from the webcam, taskbar, VPN, and text-to-speech tools, among others.
Its spy functions included remote screen-viewing, live streaming the webcam content, gaining browser passwords, recovering Proton and Nord VPN credentials, and more.
The post read that the remote microphone data access was still under maintenance suggesting that there is still some work they will be doing on the LithiumRAT.
It can alter the clock settings by hiding and showing it which draws suspicion over the group’s targeting overseas entities for unknown, malicious purposes.
It has built-in exploits for CVE-2021-42278 and CVE-2020-1472 that allowed escalated privileges.
Furthermore, the Strontium stealer can enable and disable the UAC or the User Account Control, monitor, and the task manager. It can change the wallpaper, restart the device, open a website and encypt the remote target and leave a ransom note.
Polling and voting for Strontium stealer’s LithiumRAT
The threat intelligence firm FalconFeedsio tweeted about the naming of the new RAT which would be LithiumRAT.

Going by the back-and-forth communications on the hacker forums, it can be inferred that the LithiumRAT has been a work in progress. It still lacks some features that has been worked upon.
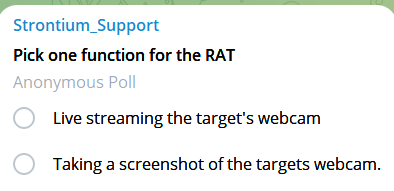
While the RAT was a work-in-progress the developers took several poles to see which features the LithiumRAT should possess.
Choosing between live streaming of the webcam and taking screenshots from the webcam to having ransomware, multi-platform clipper, and RAT capabilities were asked to be voted for, anonymously.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
