Russian Hackers’ Focus is Civilian Infrastructure
Business Continuity Management / Disaster Recovery
,
Critical Infrastructure Security
,
Cybercrime
Cybersecurity Officials See Prioritization on Infrastructure Over Military Targets

State-backed Russian hacking groups are continuing to focus less on Ukrainian military targets and much more on civilian infrastructure, Ukrainian cybersecurity officials report.
See Also: Stronger Security Through Context-aware Change Management: A Case Study
Ukraine’s lead cybersecurity defense agency, the State Service of Special Communication and Information Protection, or SSSCIP, reports that the intensity of cyberattacks aimed at Ukrainian critical infrastructure has more or less remained constant since Russia launched its full-blown invasion on Feb. 24.
Cyber incidents and cyberattacks counted so far this year by the Ukrainian Computer Emergency Response Team – CERT-UA – totaled more than 2,100, it reports.
However, “it is not military but civil infrastructure that has been the primary target for Russian hackers throughout the year,” SSSCIP says.
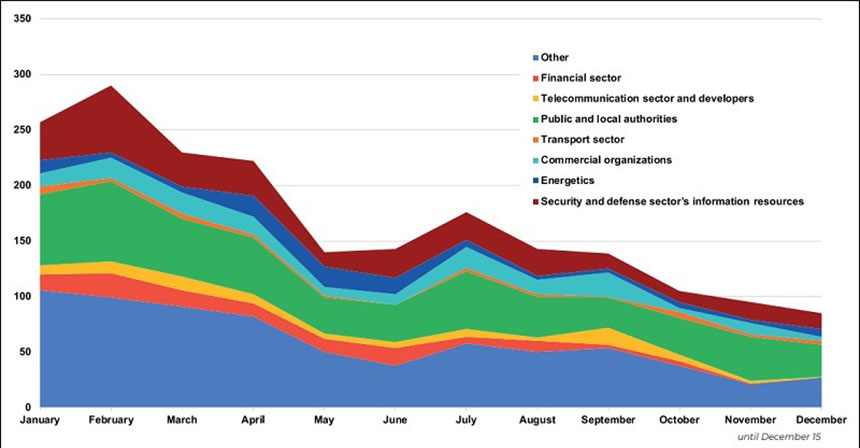
Top Targets: Public and Energy Sectors
The Ukrainian public sector was most targeted, accounting for nearly one quarter of all cases investigated by CERT-UA, followed by the energy sector. Ukrainian officials say there’s been a considerable increase over the course of the year in attacks targeting power grid operators, regional electricity distributors, customer service firms and design institutions. One challenge, it says, is that the attacks are targeting all parts of the energy supply chain, which makes them more difficult to detect and block.
Earlier this month, for example, an energy sector facility was targeted, but not directly, by hackers. “They tried to launch this attack by hacking the company developing and supplying software for the facility in question,” the SSSCIP says.
In the second half of the year, attacks targeting Ukraine’s commercial sector reportedly rose, only to be supplanted by attacks targeting the telecommunications and software development sectors, apparently again because of their facility in providing entry points to hackers.
The logistics sector has also been a target, imperiling moving critical equipment needed by both the military as well as civilians. Ransomware has been brought to bear against logistics firms too, with Microsoft in October warning that it was tracking a new type of crypto-locking malware, Prestige ransomware, that appeared to be mainly used to target the logistics sector in both Ukraine and Poland.
“Based on the results of the analysis conducted, we can assert with a high degree of certainty that Russian government-backed hackers were behind these attacks,” SSSCIP says.
Wipers, Backdoors and More
Ukrainian officials say the drivers for Russian-backed hacking attacks include espionage, psychological operations – aka PsyOps – and disinformation.
On the technical front, backdoors remain a part of Russia’s hack attack arsenal, as does wiper malware, officials say.
In August, Victor Zhora, the deputy head of SSSCIP, told Information Security Media Group that one of the biggest cybersecurity surprises of the war had been Russia’s widespread use of wiper malware, as well as its impact. As of August, he reported, “we’ve identified more than 10 different types of wipers used during the war, and it seems to me that that is not the limit (see: Ukraine’s Cyber Defense: Wipers Remain ‘Biggest Challenge’)
The most active hacking groups targeting Ukraine this year, SSSCIP says, include:
Ukraine Steps Up Training
The SSSCIP report warns that Russian hackers have continued to use phishing attacks to accomplish many of their aims. Such efforts have been aided, they say, by their impersonating and sometimes even using hacked email accounts for the SSSCIP, Ukrainian government press liaisons or CERT-UA. Accordingly, Ukraine says it’s stepped up cyber resilience training for public officials, to raise awareness not just of how to individually defend themselves on the cybersecurity front, but also relevant legal requirements and wartime considerations.
“The role of governmental agencies in ensuring cyber defense is no less important than ours as a regulatory authority,” says SSSCIP Deputy Head Oleksandr Potii. “However, handling all of this requires appropriate skills, so there should be a constant dialogue between the regulatory authority and implementing actors. This is why we initiated these training courses.”
Ukraine is also tightening cooperation with allies, including the U.S. and EU, to build a better collective cyber defense system against Russia’s online attacks (see: Zelenskyy Makes Case for Ukraine Support in Washington Trip).
In particular, the SSSCIP is working more closely with NATO’s Cooperative Cyber Defense Center of Excellence, as well as signed a memorandum of understanding for cyber defense cooperation with the National Cyber Security Directorate of Romania.






