An analysis of the sample data shared by the hackers revealed, among other details, personal and insurance-related information belonging to three GRU agents.
Since the beginning of the Russia-Ukraine conflict, both nations have experienced a series of non-stop large-scale cyberattacks targeting critical infrastructure, personal data of unsuspecting users, as well as sensitive military and banking information. Additionally, hacktivists from both sides are engaging in these attacks aligned with their respective causes.
During the ongoing conflict, a significant aspect often overlooked is the involvement of hackers motivated by financial gain. These actors, driven by profit, engage in hacking and selling data. In a recent cybersecurity incident tied to financial motivations, a threat actor targeted Rosgosstrakh (Russian: Росгосстрах), Russia’s second-largest insurance company after SOGAZ, successfully stealing a substantial amount of customer and sensitive financial data.
The individual known by the alias “Apathy” has announced intentions to sell the hacked data. Notably, the Rosgosstrakh data has emerged on well-known Breach Forums, with a price tag set at $50,000 in Bitcoin (BTC) or Monero (XMR) cryptocurrency for the extensive collection of information.
What’s in the leaked data?
The compromised data includes full access to the investment and life insurance department records dating back to 2010. The breach, which has put approximately 3 million bank statements at risk, has also compromised data on 730,000 individuals, with approximately 80,000 individuals’ Russian Social Security Numbers (SNILS) and 45,000 individuals’ complete bank routing information now in jeopardy.
The breach also includes access to all life insurance policies and contracts, as well as associated attachments such as passports and scanned documents of public officials or their immediate relatives.
The hacker additionally intends to offer prospective buyers a “full buyout” by providing complete access to Rosgosstrakh’s internal Web User Interface (UI). A full buyout refers to the complete purchase or acquisition of all rights and ownership of a product, service, or asset.
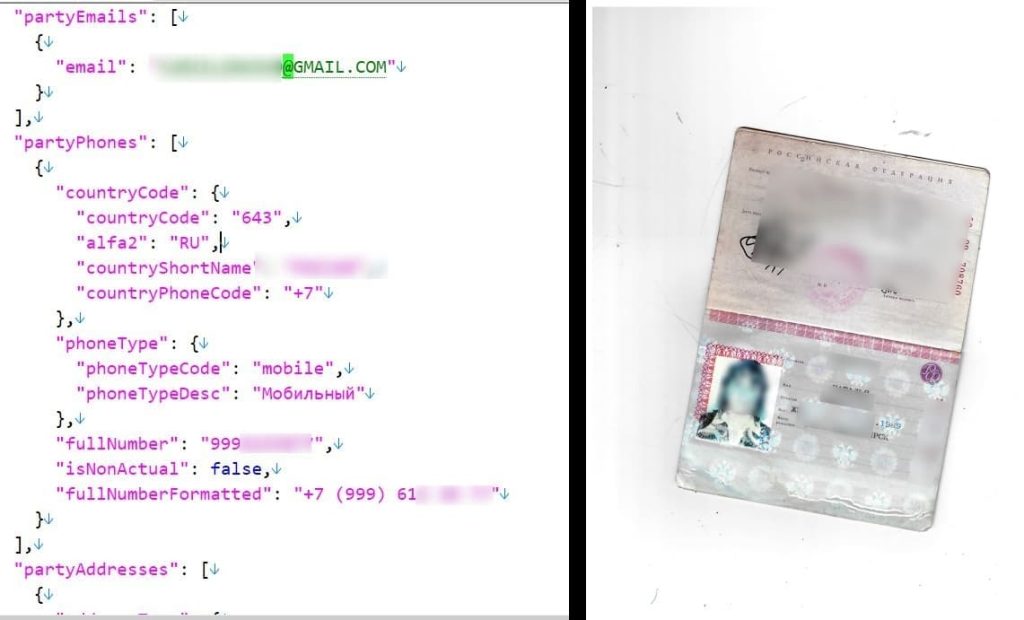
(GRU DATA) Data of Russian Military Intelligence Agents
Hackread.com has examined the sample data shared by the hacker on Breach Forums. However, another party that obtained a portion of the data from the hacker is Maia Arson Crimew, a Swiss security researcher and hacker.
Crimew disclosed acquiring an extensive 22GB of JSON data in plain-text format. The complete database comprises a staggering 400GB of data.
In a blog post, Crimew revealed their analysis of the dataset, uncovering information attributed to three GRU agents. The GRU, an entity within the Russian Armed Forces, functions as a military foreign intelligence agency situated in Russia.
Crimew’s findings contained comprehensive details about the agents, featuring their full names, dates of birth, phone numbers, email addresses, passport numbers, and specifics related to insurance coverage, particularly life insurance information.
Conclusion
Rosgosstrakh is a large and well-established company, yet it was vulnerable to a cyberattack. This demonstrates that no organization is immune to cyber threats. The Rosgosstrakh data breach is a serious incident that has exposed the personal and financial information of a large number of individuals.
It is also worth noting that the data breach could have implications for the Russian government. The fact that the data includes information on Russian military intelligence agents could be used by foreign governments to gain an advantage over Russia. Additionally, the breach could damage Russia’s reputation and make it more difficult for Russian companies to do business internationally.
RELATED HACKS
Gone: Russian Central Bank hacked; $31 million stolen
2 Russian Industrial Firms Hacked, 112GB of Data Leaked
Anonymous Leaks 128 GB of Data from Russian ISP Convex
Elite North Korean Hackers Breach Russian Missile Developer
Anonymous Hacks Central Bank of Russia; Leaks 28GB of Data
