A medium-severity vulnerability in the Iconics Suite SCADA system that could allow attackers to trigger denial-of-service conditions on critical industrial control systems.
The flaw, tracked as CVE-2025-0921, affects supervisory control and data acquisition infrastructure widely deployed across automotive, energy, and manufacturing sectors.
Vulnerability Overview
CVE-2025-0921 stems from an execution-with-unnecessary-privileges weakness in multiple services within Mitsubishi Electric Iconics Digital Solutions GENESIS64.
The vulnerability has a CVSS score of 6.5, which is classified as medium severity. Successful exploitation enables attackers to misuse privileged file system operations to elevate privileges and corrupt critical system binaries, ultimately compromising system integrity and availability.
| CVE Identifier | Vulnerability Description | CVSS Score |
|---|---|---|
| CVE-2025-0921 | Execution with unnecessary privileges vulnerability in multiple services of Mitsubishi Electric Iconics Digital Solutions GENESIS64 | 6.5 (Medium) |
The vulnerability was discovered during a comprehensive security assessment conducted by Unit 42 researchers Asher Davila and Malav Vyas in early 2024.
This finding represents one of six vulnerabilities identified in Iconics Suite versions 10.97.2 and earlier for Microsoft Windows platforms.
The researchers previously disclosed five related vulnerabilities affecting the same SCADA platform, with CVE-2025-0921 emerging as an additional threat during their investigation.
According to Mitsubishi Electric’s security advisory, the vulnerability impacts all versions of GENESIS64, MC Works64, and GENESIS version 11.00.
Iconics Suite maintains hundreds of thousands of installations across more than 100 countries, spanning critical infrastructure sectors such as government facilities, military installations, water and wastewater treatment plants, utilities, and energy providers.
Technical Exploitation Details
The vulnerability resides in the Pager Agent component of AlarmWorX64 MMX, the alarm management system that monitors industrial processes.
Attackers with local access can exploit the flaw by manipulating the SMSLogFile path configuration stored in the IcoSetup64.ini file located in the C:ProgramDataICONICS directory.
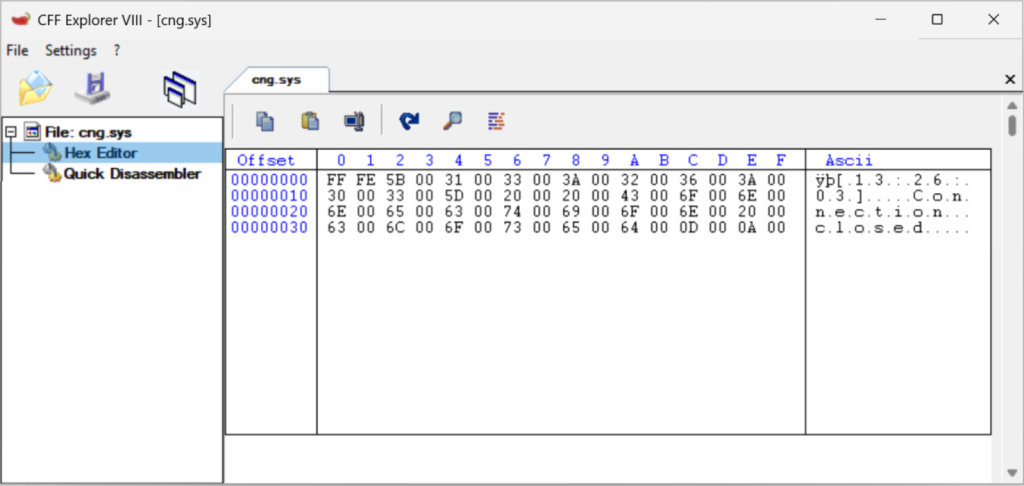
The attack chain involves creating symbolic links from the log file location to target system binaries.
When administrators send test messages or the system automatically triggers alerts, logging information follows the symbolic link and overwrites critical drivers such as cng.sys, which provides cryptographic services for Windows system components.
Upon system reboot, the corrupted driver causes boot failures, trapping the machine in an endless repair loop and rendering the OT engineering workstation inoperable.

Researchers demonstrated that exploitation becomes significantly easier when combined with CVE-2024-7587, a previously disclosed vulnerability in the GenBroker32 installer that grants excessive permissions to the C:ProgramDataICONICS directory, allowing any local user to modify critical configuration files.
However, attackers could still exploit CVE-2025-0921 independently if log files become writable due to misconfiguration, other vulnerabilities, or social engineering.
Mitsubishi Electric has released patches for GENESIS version 11.01 and later, which customers can download from the Iconics Community Resource Center.
For GENESIS64 users, a fixed version is currently under development and will be released in the near future. The vendor has indicated no plans to release patches for MC Works64, requiring customers to implement mitigations in the meantime.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.



