A new round of the weekly Security Affairs newsletter has arrived! Every week, the best security articles from Security Affairs are free in your email box.
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.
| Osiris ransomware emerges, leveraging BYOVD technique to kill security tools |
| U.S. CISA adds a flaw in Broadcom VMware vCenter Server to its Known Exploited Vulnerabilities catalog |
| 11-Year-Old critical telnetd flaw found in GNU InetUtils (CVE-2026-24061) |
| Fortinet warns of active FortiCloud SSO bypass affecting updated devices |
| U.S. CISA adds Prettier eslint-config-prettier, Vite Vitejs, Versa Concerto SD-WAN orchestration platform, and Synacor Zimbra Collaboration Suite flaws to its Known Exploited Vulnerabilities catalog |
| Investigation underway after 72M Under Armour records surface online |
| Machine learning–powered Android Trojans bypass script-based Ad Click detection |
| Critical SmarterMail vulnerability under attack, no CVE yet |
| Arctic Wolf detects surge in automated Fortinet FortiGate firewall configuration attacks |
| U.S. CISA adds a flaw in Cisco Unified Communications products to its Known Exploited Vulnerabilities catalog |
| Cisco fixed actively exploited Unified Communications zero day |
| Zoom fixed critical Node Multimedia Routers flaw |
| ACME flaw in Cloudflare allowed attackers to reach origin servers |
| Crooks impersonate LastPass in campaign to harvest master passwords |
| VoidLink shows how one developer used AI to build a powerful Linux malware |
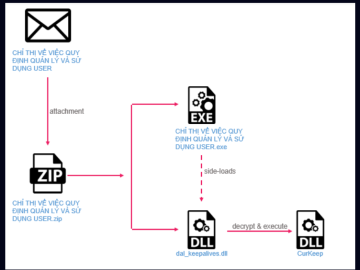
| PDFSIDER Malware – Exploitation of DLL Side-Loading for AV and EDR Evasion |
| Access broker caught: Jordanian pleads guilty to hacking 50 companies |
| Critical TP-Link VIGI camera flaw allowed remote takeover of surveillance systems |
| Telegram-based illicit billionaire marketplace Tudou Guarantee stopped transactions |
| UK NCSC warns of Russia-linked hacktivists DDoS attacks |
| Ransomware attack on Ingram Micro impacts 42,000 individuals |
| StealC malware control panel flaw leaks details on active attacker |
| Hacker pleads guilty to hacking Supreme Court, AmeriCorps, and VA Systems |
| Hacktivists hijacked Iran ’s state TV to air anti-regime messages and an appeal to protest from Reza Pahlavi |
| GootLoader uses malformed ZIP files to bypass security controls |
International Press – Newsletter
International operation of Ukraine and Germany: members of the Black Basta group were exposed
Tennessee Man Pleads in Hacking U.S. Supreme Court, AmeriCorps, and VA Health System
Tudou Guarantee winds down operations after $12 billion in transactions
Jordanian Man Admits Selling Unauthorized Access to Computer Networks of 50 Companies
Greek police arrest scammers using fake cell tower hidden in car trunk
Resurgence of a multi‑stage AiTM phishing and BEC campaign abusing SharePoint
Under Armour says it’s ‘aware’ of data breach claims after 72M customer records were posted online
ShinyHunters claim to be behind SSO-account data theft attacks
Malware
PDFSIDER Malware – Exploitation of DLL Side-Loading for AV and EDR Evasion
VoidLink: Evidence That the Era of Advanced AI-Generated Malware Has Begun
PyPI Package Impersonates SymPy to Deliver Cryptomining Malware
Osiris: New Ransomware, Experienced Attackers?
Hacking
WhisperPair
WATCH: Anti-regime activists hack Iran’s national broadcaster, transmit Pahlavi’s calls to protest
CrashFix Chrome Extension Delivers ModeloRAT Using ClickFix-Style Browser Crash Lures
Interception and Eavesdropping of Satellite Communications
Cloudflare whacks WAF bypass bug that opened side door for attackers
Cloudflare Zero-day: Accessing Any Host Globally
Arctic Wolf Observes Malicious Configuration Changes On Fortinet FortiGate Devices via SSO Accounts
Attackers With Decompilers Strike Again (SmarterTools SmarterMail WT-2026-0001 Auth Bypass)
Analysis of Single Sign-On Abuse on FortiOS
CISA Adds Actively Exploited VMware vCenter Flaw CVE-2024-37079 to KEV Catalog
Infotainment, EV Charger Exploits Earn Hackers $1M at Pwn2Own Automotive 2026
Intelligence and Information Warfare
Pro-Russia hacktivist activity continues to target UK organisations
Taiwan China Cyberattacks on Energy Sector Increased Tenfold
Threat Actors Expand Abuse of Microsoft Visual Studio Code
From Protest to Peril Cellebrite Used Against Jordanian Civil Society
APT Malware Detection Model Based on Heterogeneous Multimodal Semantic Fusion
EU considers whether there’s Huawei of axing Chinese kit from networks within 3 years
ESET Research: Sandworm behind cyberattack on Poland’s power grid in late 2025
Cybersecurity
TP-Link Patches Vulnerability Exposing VIGI Cameras to Remote Hacking
EU plans cybersecurity overhaul to block foreign high-risk suppliers
New Phishing Campaign Targeting LastPass Customers
Global Cybersecurity Outlook 2026
Specops Breached Password Report 2026
Are We Ready to Be Governed by Artificial Intelligence?
NSO Group spyware probe due to lack of cooperation from Israel
Announcement from the new TikTok USDS Joint Venture LLC
Ransomware: Tactical Evolution Fuels Extortion Epidemic
Europe Prepares for a Nightmare Scenario: The U.S. Blocking Access to Tech
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
Pierluigi Paganini
(SecurityAffairs – hacking, newsletter)