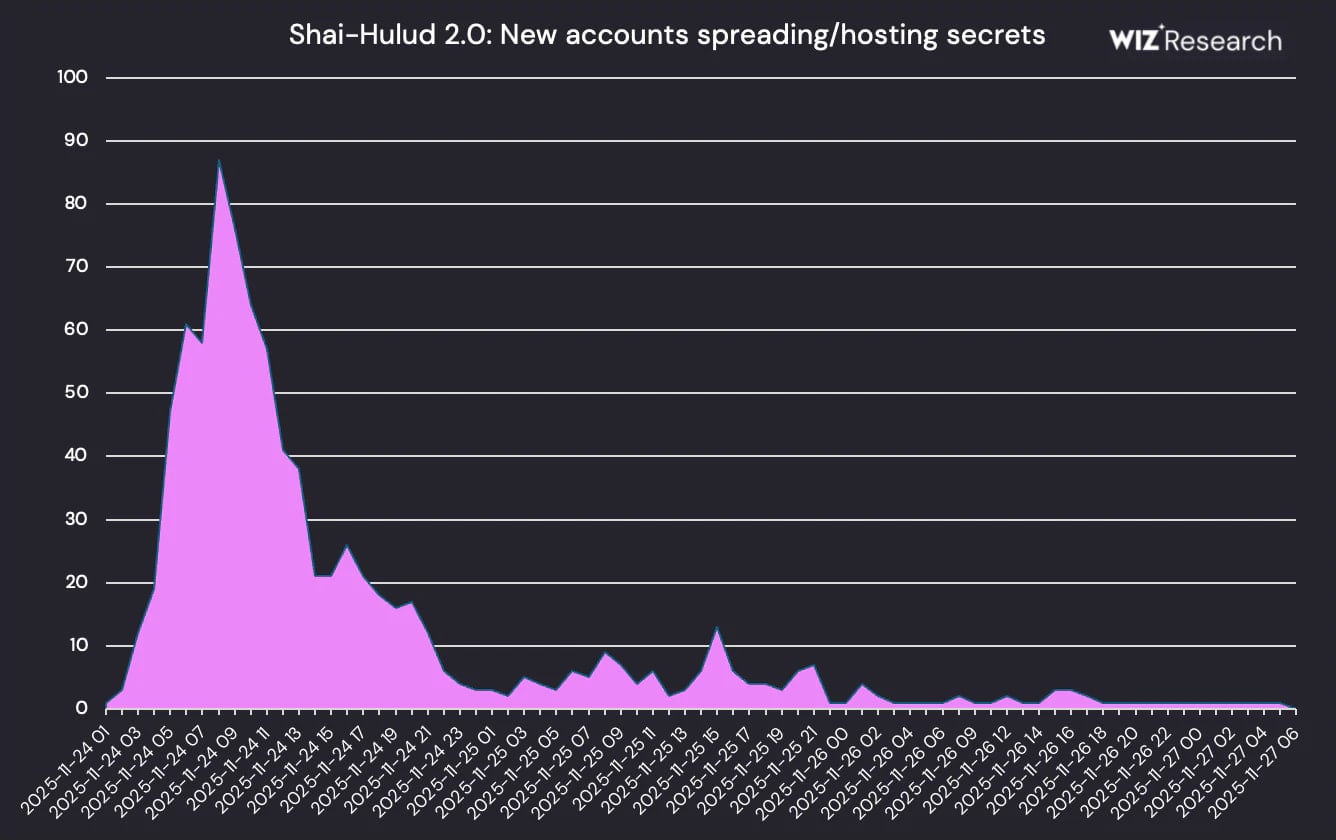
The second Shai-Hulud attack last week exposed around 400,000 raw secrets after infecting hundreds of packages in the NPM (Node Package Manager) registry and publishing stolen data in 30,000 GitHub repositories.
Although just about 10,000 of the exposed secrets were verified as valid by the open-source TruffleHog scanning tool, researchers at cloud security platform Wiz say that more than 60% of the leaked NPM tokens were still valid as of December 1st.
The Shai-Hulud threat emerged in mid-September, compromising 187 NPM packages with a self-propagating payload that identified account tokens using TruffleHog, injected a malicious script into the packages, and automatically published them on the platform.
In the second attack, the malware impacted over 800 packages (counting all infected versions of a package) and included a destructive mechanism that wiped the victim’s home directory if certain conditions were met.
Source: Wiz
Wiz researchers analyzing the leak of secrets that the Shai-Hulud 2.0 attack spread over 30,000 GitHub repositories, found that the following types of secrets have been exposed:
- about 70% of the repositories had a contents.json file with GitHub usernames and tokens, and file snapshots
- half of them had the truffleSecrets.json file containing TruffleHog scan results
- 80% of the repositories had the environment.json file with OS info, CI/CD metadata, npm package metadata, and GitHub credentials
- 400 repositories hosted the actionsSecrets.json with GitHub Actions workflow secrets
Wiz notes that the malware used TruffleHog without the ‘-only-verified’ flag, meaning that the 400,000 exposed secrets match a known format and may not be valid or usable anymore.
“While the secret data is extremely noisy and requires heavy deduplication efforts, it still contains hundreds of valid secrets, including cloud, NPM tokens, and VCS credentials,” explained Wiz.
“To date, these credentials pose an active risk of further supply chain attacks. For example, we observe that over 60% of leaked NPM tokens are still valid.”
Analysis of 24,000 environment.json files showed that roughly half of them were unique, with 23% corresponding to developer machines, and the rest coming from CI/CD runners and similar infrastructure.
The data compiled by the researchers shows that most of the infected machines, 87% of them, are Linux systems, while most infections (76%) were on containers.
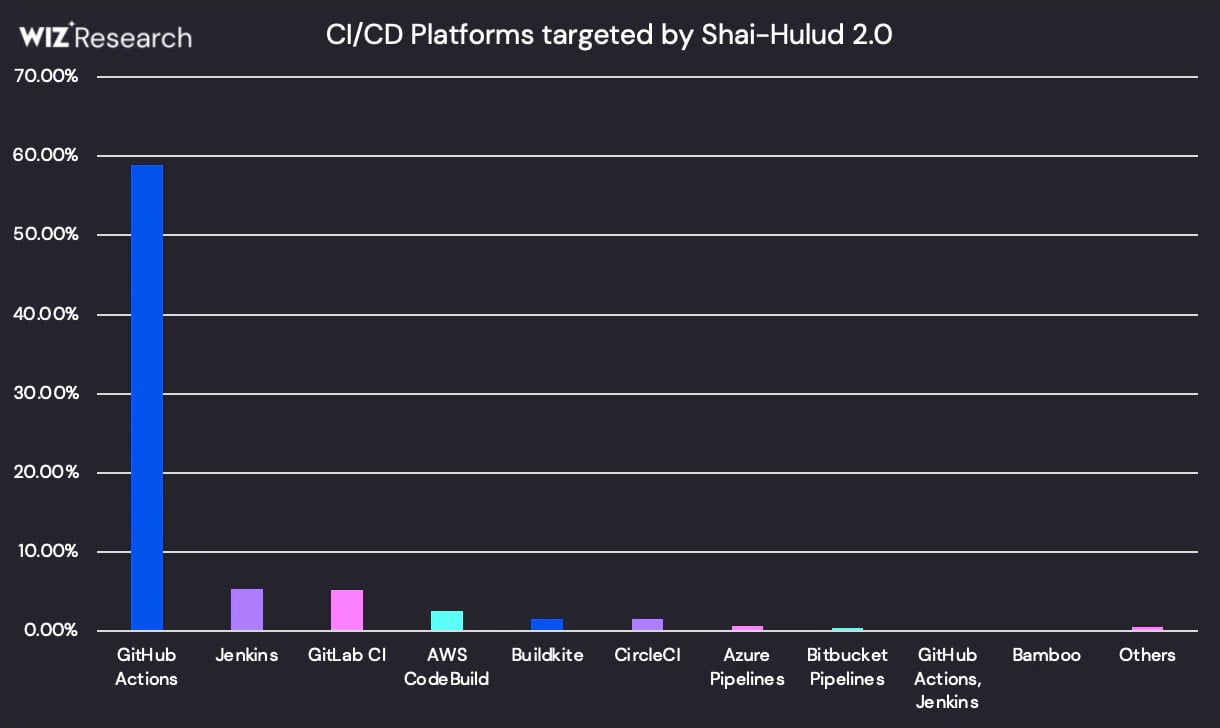
Regarding the CI/CD platform distribution, GitHub Actions led by far, followed by Jenkins, GitLab CI, and AWS CodeBuild.
Source: Wiz
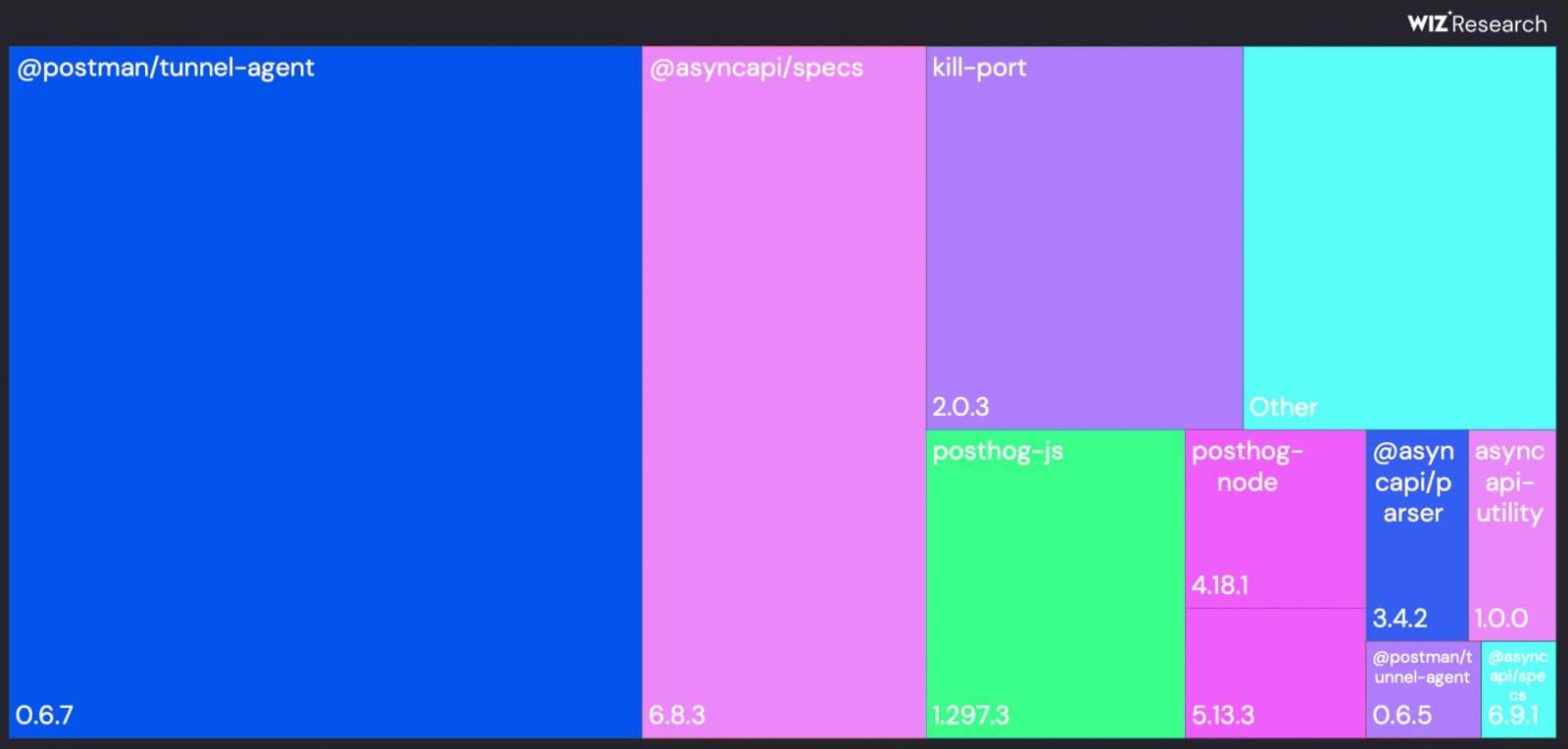
Looking at the infection distribution, Wiz researchers found that the top package was @postman/tunnel-agent@0.6.7, followed by @asyncapi/specs@6.8.3. These two packages together accounted for more than 60% of all the infections.
Source: Wiz
Because of this focus, the researchers say that the Shai-Hulud impact could have been greatly reduced if a few key packages had been identified and neutralized early on.
Similarly, concerning the infection pattern, 99% of instances came from the preinstall event running node setup_bun.js, and the very few exceptions were likely testing attempts.
Wiz believes that the perpetrators behind Shai-Hulud will continue to refine and evolve their techniques, and predicts that more attack waves will emerge in the near future, potentially leveraging the massive credential trove harvested so far.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.




