“To improve the security of their connected systems, every corporation should have a vulnerability disclosure policy that allows them to receive security submissions from the outside world.” – Jeff Massimilla, Chief Product Cybersecurity Officer, General Motors
Every organization can benefit from providing a clear, legal, and easy path for someone to report a potential bug or security gap to them. As the U.S. Department of Defense notes, “The security researcher community regularly makes valuable contributions to the security of organizations and the broader Internet, and DoD recognizes that fostering a close relationship with the community will help improve our own security.”
You could even go so far as saying not having a vulnerability disclosure policy amounts to cybersecurity negligence. If you’re unfamiliar with responsible disclosure policies, take a look at the first part of this series, What a Vulnerability Disclosure Policy is and Why You Need One.
If you still don’t have one in place, you’re not alone. In fact, our research shows that 93% of companies on the 2017 Forbes Global 2000 list of the world’s most valuable public companies do not have a known VDP. Progress is being made, however. Gartner recently predicted that 50% of enterprises will have crowdsourced security solutions by 2022.
In this post, we look at what the process looks like without a dedicated reporting method, why ad hoc reporting solutions add unnecessary risk, how you can control what used to be chaotic in a streamlined workflow with HackerOne Response, and how a team of experts is ready to help you reduce risk while still accelerating resolution times.
Life Without a Dedicated Reporting Method
When someone discovers a potential vulnerability on your website or in your products, the lack of an easy-to-find responsible disclosure policy means you’ll probably never know — or worse, others will know before you do. But, even if a hacker does manage to contact your organization, the lack of a structured process typically adds delays, or may even prevent the report from ever reaching the appropriate teams.
Here’s one scenario to consider: A person stumbles across a potential vulnerability and wants to alert you. They’ll look for a contact method, finding maybe an email address on your website for info@ or sales@. Or maybe they’ll send a direct message to your organization’s Twitter or Facebook account. Regardless, the message may or may not get to a person, and even if it does, that person may or may not know what to do with it.
The result, nearly every time, is that nothing happens…except that the vulnerability remains unfixed.
Sometimes, a finder becomes frustrated with the lack of a clear vulnerability reporting channel and publicly discloses it. Maybe they tag your organization on social media, alerting potentially tens of thousands of individuals to your security gap. It happens in an instant, long before you have time to investigate or even begin working on a fix.
Yes, that’s the worst case scenario. But even if you do have a VDP in place, are you sure that it’s effective?
Ad Hoc Reporting Solutions Add Risk
The key to any reporting system is getting the incoming reports into the hands of the right people as efficiently and securely as possible.
Many organizations choose to use a security@[myorganization].com email address as their VDP’s reporting method. They rely on a revolving team to check and appropriately triage incoming emails, then copy and paste that information into another reporting or bug tracking system. Still others might use a customer support solution to manage incoming reports, relying on the system and the customer support staff to appropriately route and track security-related messages.
These cobbled-together solutions take tools designed for other teams and other types of communications and try to apply them to a highly technical, highly specific task. They rely on decision-making from non-security workers, error-prone manual data transfers, and faith that the process won’t lose or delay the discovery of a catastrophic vulnerability.
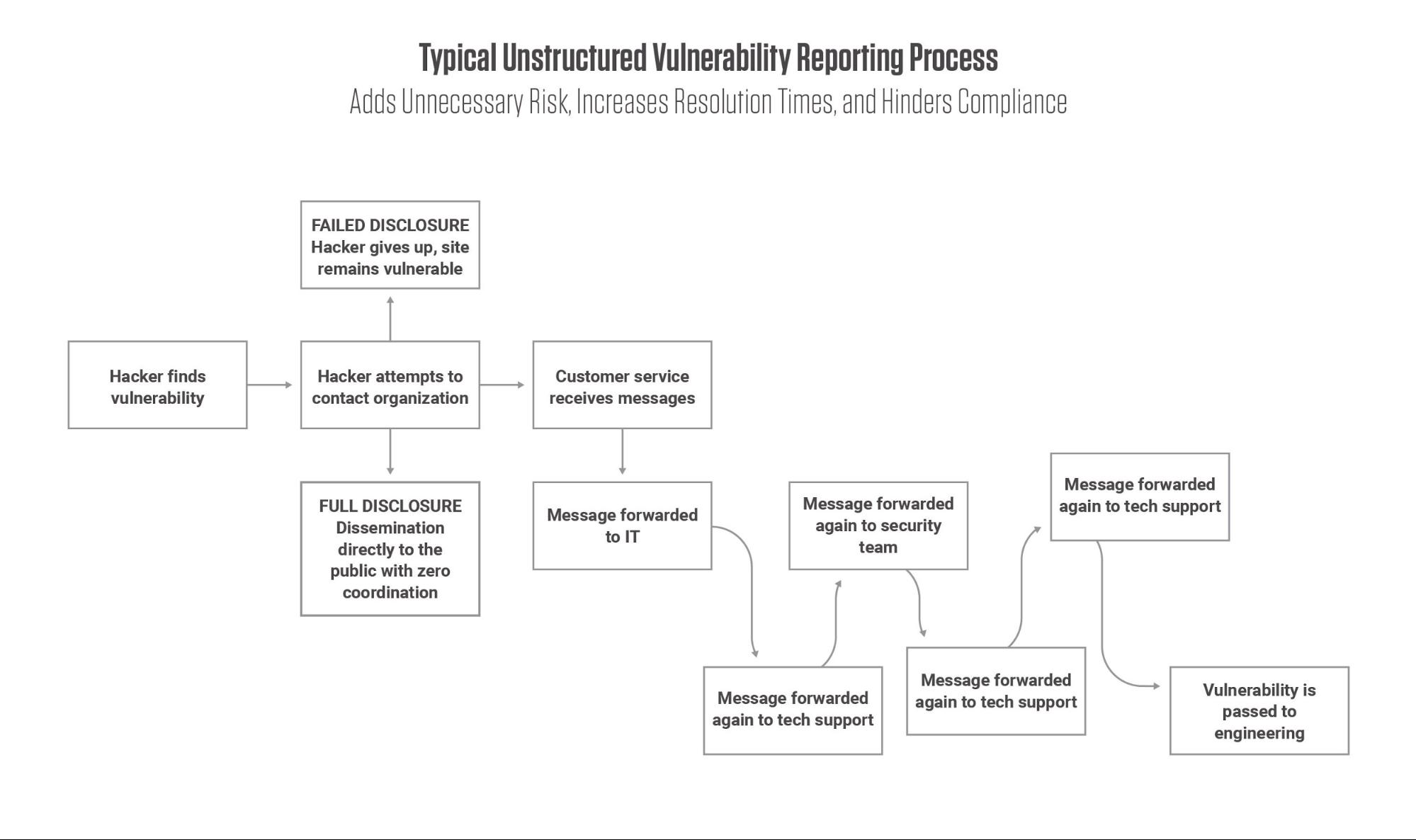
With multiple points of contact and modes of communication, including email, social media, and customer support channels, you risk losing track of valuable vulnerabilities unless personnel at every potential touchpoint are adequately trained on what to do when they receive a report.
Even then, when reports arrive via these unconventional channels, they risk being delayed or lost before the appropriate teams are alerted. Those precious days or weeks could be the difference between proactively resolving a vulnerability and protecting your brand, customers, and data, or allowing a security breach and the related fallout and penalties.
Furthermore, with security and data issues under the microscope more often than ever before, the issue of auditing and compliance add even more stress to an already fragile setup. Risk and compliance professionals know the value of having in place a defined process with easy-to-understand documentation and robust controls to manage users and their access.
Relying on an ad hoc vulnerability reporting system adds unnecessary risk to a process meant to minimize risk and maximize speed. A solution with built in compliance is the obvious way to go.
Auditability and compliance are critical, as responsible disclosure policies and their accompanying audit trails are now seen as vital components of any modern compliance engine, especially in the age of GDPR. The Centre for European Policy Studies (CEPS) initiated a task force to define vulnerability disclosure guidelines for the European Union. Their recommendations state that since “irresponsible handling of vulnerabilities could lead to personal data breaches falling within the scope of GDPR”, VDPs should be seen as one of the “necessary tools to mitigate the relevant risks.”
Being aligned with ISO 29147 and SOC 2, especially for cloud-based service providers, is also increasingly important, and compliance with EU-U.S. and Swiss-U.S. Privacy Shield Frameworks offers additional data accountability. The resulting process tracking, auditability, conversation threads, and contextual vulnerability information keeps both reviewers and auditors happy.
Streamline Your VDP with HackerOne
“We need to move to a world where…all companies providing internet services and devices adhere to a vulnerability disclosure policy.” – Julian King, Security Union Commissioner, European Commission
HackerOne Response is our turnkey solution offering enterprise-grade security and conformance with ISO-29147 (vulnerability disclosure) and ISO-30111 (vulnerability handling). It allows vulnerability management teams to work directly with external third-parties to resolve critical security vulnerabilities before they can be exploited. HackerOne Response provides a secure platform and integrates easily with existing systems and workflows.
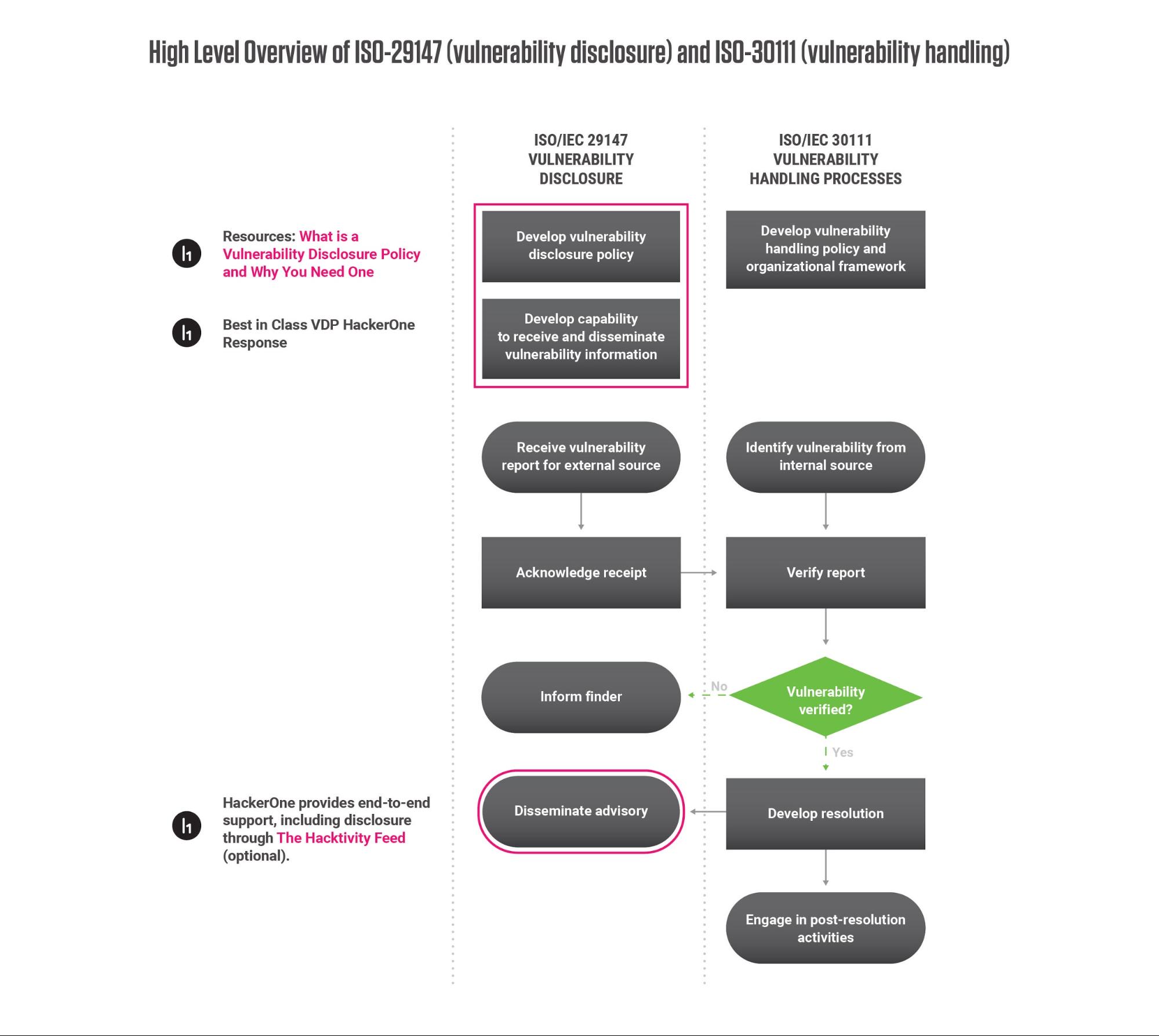
HackerOne Response provides three ways for hackers to submit vulnerabilities to you and your team, empowering you to choose one or more to fit your needs.
Email forwarding lets you receive emails in your HackerOne inbox and manage reports directly through HackerOne. If you already have an existing security email alias, email forwarding is a simple, effective, and fast way to start with HackerOne Response. However, with email forwarding alone, your program will not be on the HackerOne directory and will get minimal attention from HackerOne hackers.
Embedded submission forms can be easily added to your website and let you prescribe the precise information you want in each report, which streamlines submissions and management. Receiving vulnerability reports via embedded forms also allows for anonymous submissions — something that appeals to some hackers.
While both are great ways to receive reports, neither email forwarding nor embedded forms provide visibility into your VDP with the HackerOne community.
A standard VDP policy page listed on the HackerOne directory offers the best visibility for your VDP. It ensures maximum exposure to our hacker community, and the directory’s numerous filters and search options make it easy for hackers to find your VDP, which often increases the number of reports you receive.
Regardless of the option or options you choose, our Controlled Launch service ensures a seamless VDP launch, with minimum risk of overwhelming your IT,Engineering, and Security teams.
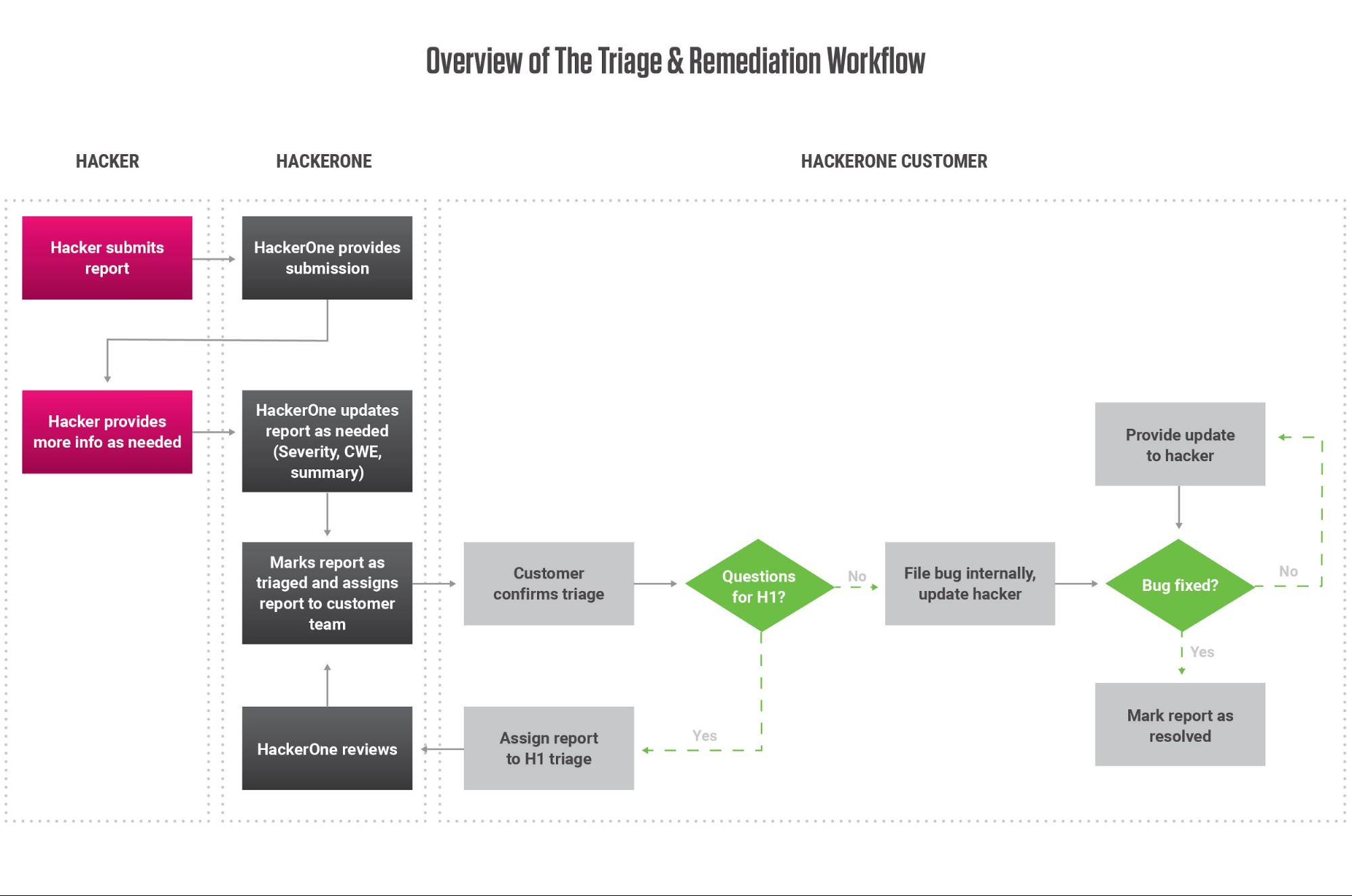
With HackerOne’s structured approach to vulnerability reporting and our expert guidance, you can streamline your existing process and build a faster, more dependable receipt and resolution machine.
Reduce Risk While Accelerating Resolution
HackerOne Response is a single solution that helps you simplify your disclosure process, reduce risk across your organization, and avoid the unpleasant surprise of an unknown vulnerability going public or getting exploited.
But HackerOne Response also elevates the experience for the finders, as well. It not only gives them a clear and simple method for reporting potential bugs, it allows you to respond to and communicate with them with ease. Simply responding to them with acknowledgement of receipt is something few ad hoc solutions can guarantee. Furthermore, requesting more information or communicating with finders on disclosure timelines is far easier through a dedicated system. Finders have a one-stop location to see the status of their report and all related communications.
But all of this assumes you already have a process in place for receiving and managing incoming reports. If you’re still not at that point, or if your current process is inadequate, HackerOne can help there, too.
HackerOne’s vast experience, such as working with Auto-ISAC to offer VDP workshops and other Fortune 500 companies, is available to help you build or improve your VDP process, or to educate your industry. We’ve also published hundreds of vulnerability disclosure policies, and work closely with organizations of all sizes and across industries to publish vulnerability reports.
Our team will walk you through how best to craft a policy, what to expect in your first few months, and why our platform is far superior to other alternatives. Your team will never walk alone—whether facing critical vulnerabilities or curious finders. Our customers also have access to communications support, technical assistance, hacker mediation, and more.
HackerOne’s leadership and advocacy of VDPs had also resulted in the creation of a library for related expertise and thought leadership. Our growing collection of resources, created by our internal team as well as various government agencies, industry groups, and academia, is available to help answer questions and provide guidance to all.
Next Step: Getting Started
Defining your VDP and the related process isn’t easy, but it can be with our help. Stay tuned for the full wrap-up ebook where we’ll look at how to put all of the pieces of a VDP together to launch a successful program at your organization. Interested to learn more about HackerOne Response now? Great, get in touch with us today.
