A newly identified advanced persistent threat (APT) campaign, dubbed “Swan Vector” by Seqrite Labs, has been targeting educational institutions and mechanical engineering industries in East Asian nations, particularly Taiwan and Japan.
Discovered in April 2025, this campaign leverages intricate social engineering tactics, primarily through spearphishing attachments disguised as resumes and financial documents.
The initial infection vector is a malicious ZIP file named “歐買尬金流問題資料_20250413 (6).rar” (translated as “Oh My God Payment Flow Problem Data – 2025/04/13 (6)”).

Inside, a malicious LNK file, such as “詳細記載提領延遲問題及相關交易紀錄.pdf.lnk” (Detailed Record of Withdrawal Delay Issues), triggers a multi-stage malware deployment by executing a DLL implant via the LOLBin rundll32.exe.
This campaign showcases a highly technical approach with a four-stage infection chain designed to evade detection and establish persistence using advanced techniques like DLL sideloading, API hashing, and direct syscalls.
Technical Infection Breakdown
The Swan Vector campaign unfolds through a meticulously crafted infection chain.
In the first stage, the malicious LNK file spawns rundll32.exe to execute a disguised DLL implant named “Pterois,” masqueraded as “Chen_YiChun.png.”
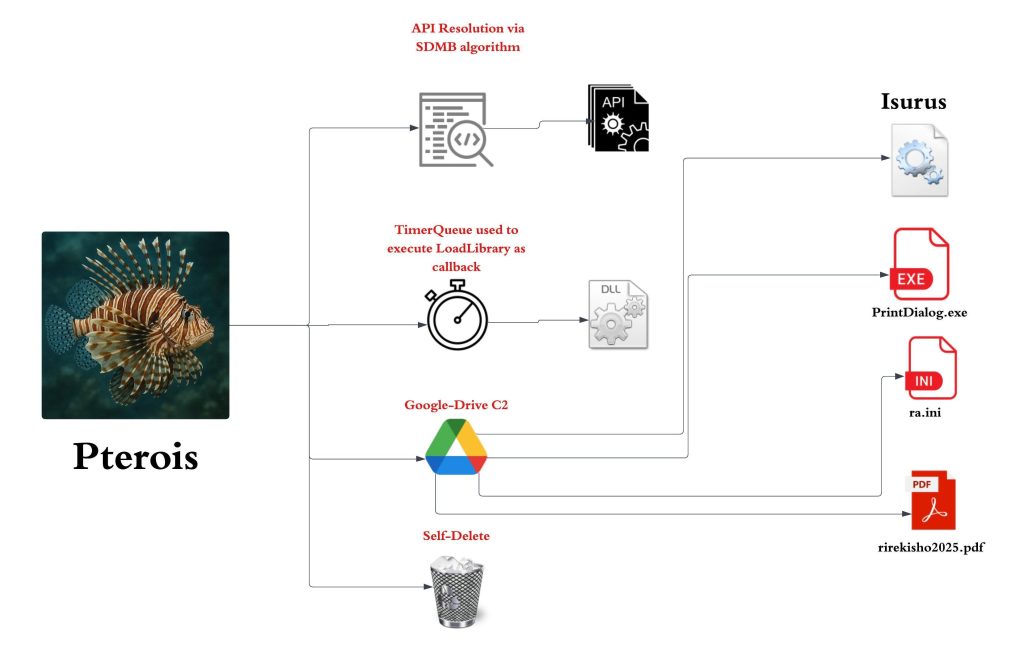
Pterois employs dynamic API resolution via Process Environment Block (PEB) walking and SDBM hashing to load necessary functions stealthily from libraries like NTDLL and Kernel32.
It then abuses Google Drive as a command-and-control (C2) server, authenticating with OAuth credentials to download additional payloads, including decoy PDFs like “rirekisho2025.pdf” (a Japanese CV), and further implants to the Temp directory.
Pterois concludes its role by self-deleting using a delayed cmd.exe process. The subsequent stages involve another implant, “Isurus,” loaded via DLL sideloading with a legitimate binary, PrintDialog.exe.
Isurus resolves APIs using CRC32 hashing and executes encrypted Cobalt Strike shellcode from “ra.ini” in memory via syscall-based techniques, ensuring minimal forensic footprints.
The final stage deploys a Cobalt Strike beacon, communicating over infrastructures hosted in Japan (e.g., IP 52.199.49.4:7284), highlighting the campaign’s reliance on sophisticated post-exploitation tools.
Threat Actor Insights
According to the Report, Seqrite Labs attributes Swan Vector to an East Asian threat actor with medium confidence, noting similarities with tactics used by groups like Winnti, Lazarus, and APT10, especially in DLL sideloading against executables like PrintDialog.exe and wmiapsrv.exe.
Active since December 2024, the actor targets hiring entities with CV-based lures and employs evasion methods such as obfuscated files, process injection, and indicator removal.
Infrastructure analysis reveals Google Drive misuse for C2 operations, exposing sensitive details like Gmail accounts (“swsanavector42@gmail.com”) and scheduled implants for future campaigns.
This suggests an ongoing threat evolution, with potential exploitation of applications like Python and OneDrive launchers.
Indicators of Compromise (IOCs)
| Type | Filename/IP | SHA-256/Value |
|---|---|---|
| Decoy PDF | rirekisho2021_01.pdf | 8710683d2ec2d04449b821a85b6ccd6b5cb874414fd4684702f88972a9d4cfdd |
| Decoy PDF | rirekisho2025.pdf | 8710683d2ec2d04449b821a85b6ccd6b5cb874414fd4684702f88972a9d4cfdd |
| IP Address | 52.199.49.4:7284 | – |
| Malicious Implant | Chen_YiChun.png | de839d6c361c7527eeaa4979b301ac408352b5b7edeb354536bd50225f19cfa5 |
| Malicious Implant | PrintDialog.dll | a9b33572237b100edf1d4c7b0a2071d68406e5931ab3957a962fcce4bfc2cc49 |
| Shellcode | ra.ini | 0f303988e5905dffc3202ad371c3d1a49bd3ea5e22da697031751a80e21a13a7 |
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



