The telecommunications sector, a cornerstone of national infrastructure, continued to remain under the radar of both ransomware and nation-state actors in 2025, revealed Cyble’s Telecommunications Sector Threat Landscape Report 2025.
The convergence of high-value subscriber data, geopolitical relevance, and complex digital ecosystems made the industry a persistent focal point for a wide spectrum of threat actors, including ideologically driven hacktivist groups.
“Telecommunications networks sit at the intersection of digital trust, national security, and everyday life. As threat actors continue to become more coordinated and persistent, telecom providers are no longer just service operators—they need to become frontline defenders of critical infrastructure,” said Mandar Patil, Founding Member & SVP at Cyble.
Why the Telecommunication Sector Remains a Prime Target
Telecom organizations were consistently targeted for their extensive repositories of Personally Identifiable Information (PII), including call records, billing details, and customer credentials. This data carries high resale value in underground markets, where compromised network access and customer databases are traded as commodities. The strategic importance of telecommunication networks in geopolitical conflicts further increased their attractiveness, as disruptions can have far-reaching economic and societal consequences.
Exposure through internet-facing infrastructure and reliance on third-party service providers amplified risk across the sector. These factors allowed threat actors to exploit vulnerabilities at multiple points, enabling both immediate financial exploitation and long-term network persistence.
Ransomware Activity and Dominant Threat Groups

Cyble documented 444 security incidents affecting the global telecommunication sector in 2025, including 90 confirmed ransomware attacks. Ransomware activity has increased fourfold since 2021. A total of 34 ransomware groups were identified, though the majority of attacks were driven by a small number of highly active actors.


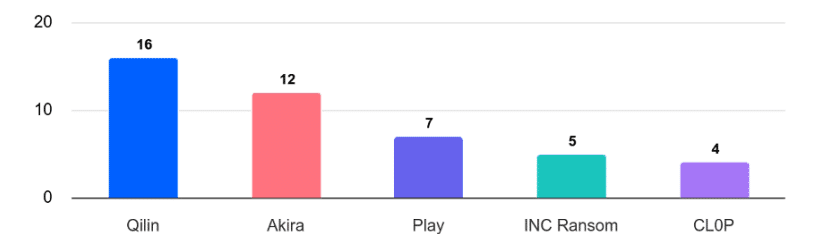
The most prolific groups, Qilin, Akira, and Play, accounted for nearly 39% of all observed incidents. Qilin led with 16 attacks, primarily targeting organizations in the United States while expanding its operations into Europe and Asia.
Supply Chain Impact and Regional Trends
The impact of cyberattacks extended across the entire telecommunication ecosystem. While major carriers such as AT&T and Orange were among the most visible victims, threat actors also targeted internet infrastructure providers and manufacturers of communications equipment. This approach disrupted operations across interconnected systems, increasing the overall impact of ransomware campaigns.

Regionally, the Americas experienced the highest number of incidents, with the United States accounting for 47 attacks. Several telecom companies, including Verizon, AT&T, and Lumen Technologies, had reported breaches ahead of the U.S. elections in late 2024. In 2025, opportunistic actors continued to monetize data believed to have been exfiltrated during those earlier intrusions, particularly large volumes of customer PII.
Nation-State Espionage and Hacktivist Disruption
Beyond financially motivated crime, nation-state actors played a critical role in shaping the threat landscape. The China-linked Salt Typhoon campaign demonstrated sustained espionage efforts against global telecommunication providers by exploiting vulnerabilities in network-edge devices from vendors such as Cisco and Fortinet. These intrusions focused on long-term surveillance and the theft of sensitive call records, compromising hundreds of organizations.
Geopolitically motivated hacktivism further contributed to disruption across the sector. Pro-Russian groups claimed intrusions into Ukrainian telecommunication infrastructure, using Distributed Denial-of-Service (DDoS) attacks, website defacements, and data leaks as part of broader ideological campaigns.
Persistent Pressure and Emerging Patterns
A defining trend in 2025 was the sustained, year-long activity of dominant ransomware groups. Qilin, in particular, maintained a consistent attack tempo throughout the year. One notable incident involved a U.S.-based telecom company appearing on the leak sites of both INC Ransom and Qilin within the same month. Additionally, isolated late-year activity linked to LockBit suggested residual operations by affiliates despite earlier law enforcement disruptions.
Overall, the telecommunication sector in 2025 faced a highly hostile environment marked by ransomware concentration, nation-state espionage, and an active underground economy trading stolen data and access.
“What we are witnessing is not a series of isolated attacks, but a sustained campaign against the telecom ecosystem. Organizations that fail to prioritize visibility, resilience, and supply-chain security will continue to face compounded risk in an increasingly contested cyber landscape,” Patil concluded.
For deeper insights into ransomware activity, nation-state threats, and telecom security risks, check out Cyble’s Telecommunications Sector Threat Landscape Report 2025.
