A worrying shift in the tactics of “Transparent Tribe,” a notorious threat group also known as APT36. Historically focused on Indian government, defense, and educational sectors, the group has now expanded its scope to target India’s growing startup ecosystem.
This new campaign uses sophisticated lures themed around real startup founders to infect victims with the “Crimson RAT” malware.
Active since 2013 and widely linked to Pakistan-based actors, Transparent Tribe usually focuses on espionage against military and diplomatic targets.
The hackers are specifically targeting startups involved in OSINT (Open Source Intelligence) and cybersecurity.
However, TRU’s recent findings indicate the group is now hunting for intelligence within private companies.
These companies often collaborate with government bodies and law enforcement agencies. By compromising these startups, the hackers likely aim to access sensitive government data indirectly.
It is a classic “supply chain” style approach: if you cannot hack the government directly, hack the private vendors they trust.
The Transparent Tribe Lure
The attack begins with a spear-phishing email containing an ISO file attachment named “MeetBisht.iso.”
To make the email appear legitimate, the hackers used decoy materials referencing a real Indian startup, “Voldebug,” and its founder.
When a victim opens the ISO file, they see what looks like an Excel shortcut (LNK file). However, clicking this shortcut does not open a spreadsheet. Instead, it triggers a hidden chain of events:
- A hidden batch script runs in the background.
- A decoy document pops up to distract the user.
- The “Crimson RAT” malware is silently installed on the computer.
The malware used in this campaign is a Remote Access Trojan (RAT). The version analyzed by Acronis has a distinct feature: it is artificially inflated to a massive 34MB size.

The hackers stuffed the file with “garbage data” to trick antivirus systems, as many security scanners are designed to skip large files to save processing time.
Once active, Crimson RAT gives the attackers total control over the infected machine. Its capabilities include:
- Surveillance: Recording the screen, turning on the webcam, and recording audio via the microphone.
- Theft: Listing all drives, searching for specific files, and uploading stolen data to the hackers.
- System Control: Killing running processes and executing new commands.
The malware uses a custom communication method (TCP protocol) to talk to its command-and-control server, making it harder for standard network monitors to spot the traffic.
Connecting the Dots
Acronis researchers are highly confident that Transparent Tribe is behind this attack. The digital fingerprints left behind including specific server infrastructure hosted in the United States and the reuse of code from previous attacks match the group’s history.
The malicious LNK, which was uploaded under the name Meet Bishkt.xlsx.lnk, had also been uploaded as Evidance.pdf.lnk.
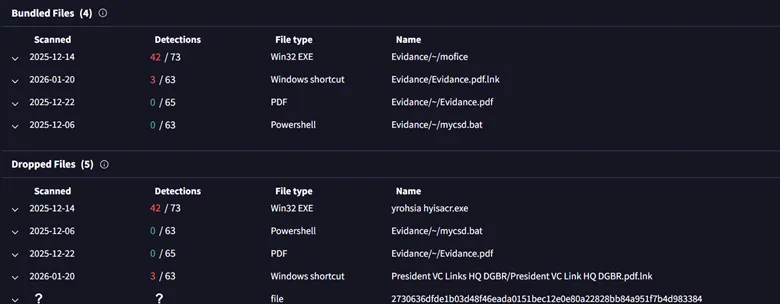
Interestingly, the researchers also found a “signature” mistake: the hackers repeatedly misspelled the word “Evidence” as “Evidance” in their file names. This spelling error has been seen in previous campaigns targeting the Indian government.
This campaign serves as a warning that India’s startups are no longer flying under the radar. Because of their proximity to government operations and law enforcement, these agile companies are now high-value targets for state-sponsored espionage.
Cybersecurity leaders in the startup sector must recognize that they are now on the digital frontline.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




