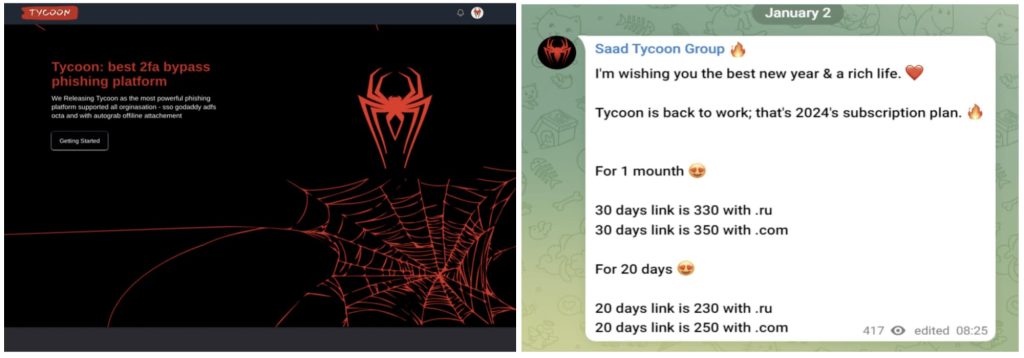
Tycoon and Storm-1575 groups are identified as key players, with Tycoon offering MFA bypass as a service and Storm-1575 targeting Microsoft 365 credentials.
Public schools across the United States are facing a surge in sophisticated phishing campaigns, according to a new report by PIXM, a cybersecurity firm specializing in artificial intelligence solutions.
Threat actors launch targeted spear phishing attacks using stealthy attack patterns to target officials at large US school districts, bypassing MFA protections.
The report highlights a worrying trend: attackers are increasingly employing tactics to bypass Multi-Factor Authentication (MFA), a security measure previously thought to offer robust protection.
Since December 2023, a surge in MFA-based phishing campaigns targeting US teachers, staff, and administrators has been observed, using dadsec and Phishing-as-a-Service (PhaaS) platforms to compromise administrator email accounts and deliver ransomware, researchers noted.
Tycoon and Storm-1575
PIXM discovered phishing activity in November 2023 and linked it to Tycoon and Storm-1575 threat groups. These groups were singled out because of their common attack pattern. Both actors use social engineering techniques, spoofing emails to appear legitimate and using AiTM (Adversary-in-the-Middle) phishing to bypass MFA tokens and session cookies.
They also create customized login experiences and use dadsec and phisingkit PhaaS services to point at legitimate sites. Their infrastructure, including C2 servers, domain generation algorithms, legitimate hosting services, and SSL certificates, allows them to control large numbers of phishing websites and avoid detection.
For your information, The Tycoon Group’s PaaS, available on Telegram for just $120, boasts key features like bypassing Microsoft’s two-factor authentication. On the other hand, Microsoft identifies Storm-1575 as a threat actor engaging in phishing campaigns through the Dadsec platform. They employ numerous Domain Generated Algorithm domains to host credential harvesting pages, targeting global organizations to extract Microsoft 365 credentials.
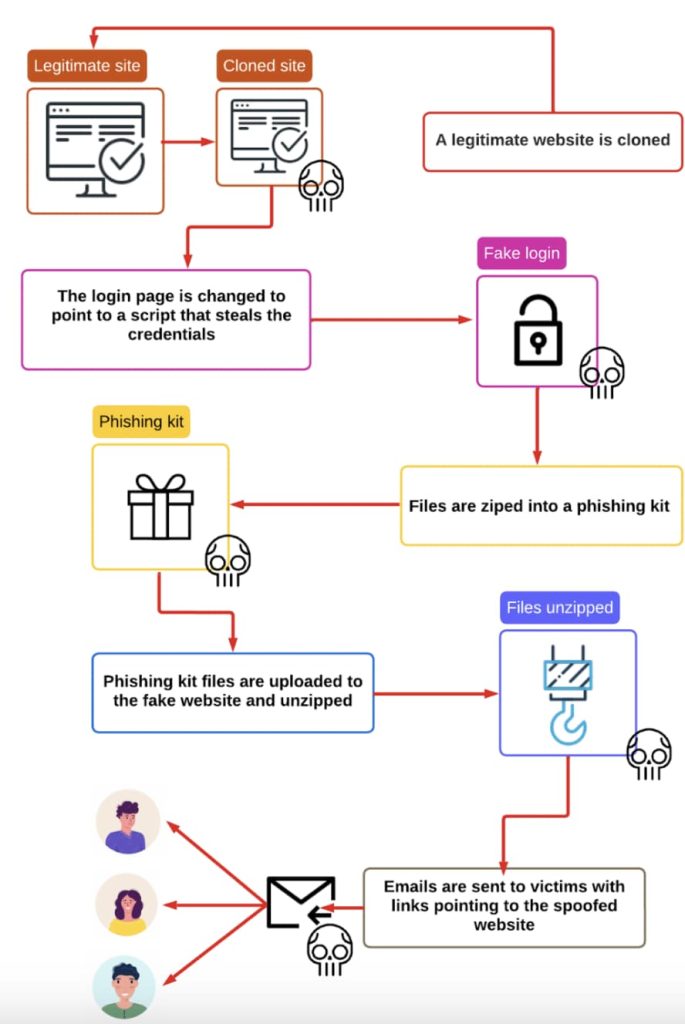
In the attacks, as detailed by PIXM in a blog post, targeted officials received phishing emails prompting them to update passwords. This led to encountering a Cloudflare Captcha and a spoofed Microsoft password page. If unthwarted, attackers would forward passwords to legitimate login pages, requesting two-factor authentication codes, and bypassing MFA protections.
Common targets include the Chief of Human Capital and multiple finance and payroll administrator accounts. Some attacks attempted to alter Windows registry keys, potentially infecting machines with malicious scripts. The attacks concealed their tracks using stealth tactics like hiding behind Cloudflare infrastructure and spinning up new domains.
The use of CAPTCHAs in phishing attacks can delay the delivery of the payload and provide a sense of legitimacy to end users. However, there is also a potential for malicious trojan activity, such as modifying Windows registry keys for the VBS file format and injecting a malicious file’script.vbs’. These attacks can be used for malware installation, ransomware, and data exfiltration.
Schools, Most Targeted Industry
While schools are the most targeted industry by ransomware gangs, student data has also been a prominent prey of cybercrime, but the extensiveness of data loss noticed recently is unprecedented. It is estimated that over 900 schools were targeted in MOVEit-linked cyber attacks.
A data leak involving Raptor Technologies in January 202, reported by cybersecurity researcher Jeremiah Fowler, exposed around 4,024,001 sensitive records belonging to students, parents, and staff, raising concerns about student privacy and school safety.
Just one month later, in February 2024, Fowler discovered a non-password-protected database storing 210,020 records or 153.76 GB of data, containing sensitive information like full names, addresses, phone numbers, and tax records of students and parents, associated with the Online Voucher Application.
To protect against such phishing attacks, organizations should identify high-priority staff with sensitive access or regular communication patterns, invest in tailored awareness efforts, arm users with caution against links and websites prompting MFA tokens and CAPTCHAs, and implement proactive AI-driven protections at the browser and email layers.
RELATED TOPICS
- Data Leak Exposes 572 GB of Student, and Faculty Info
- 100s of schools at risk after Magecart attack on Wisepay
- Iranian APT group hits schools, universities in phishing attacks
- NIST Releases Cybersecurity Framework 2.0: Guide for All Firms
- Conti ransomware gang demanded $40m from US school district
