The United States has imposed sanctions on a cybercrime network responsible for operating a massive residential proxy botnet service to combat cybercrime.
This network, 911.re, has been implicated in various illicit activities. It leverages residential IP addresses to anonymize malicious traffic and evade detection.
The 911.re Network
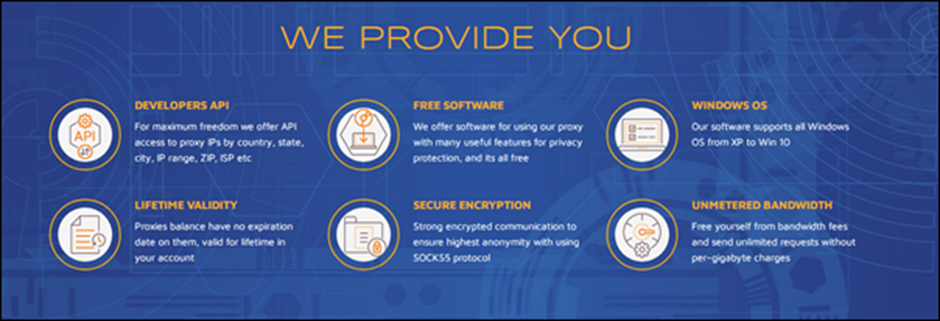
The 911.re service, a Residential Proxies As A Service (RPAAS) platform, has been operational since early 2018.
According to the U.S. DEPARTMENT OF THE TREASURY reports, It allows users to rent residential IP addresses, making their internet traffic appear as if it originates from legitimate residential users.
All-in-One Cybersecurity Platform for MSPs to provide full breach protection with a single tool, Watch a Full Demo
While such services can be used for legitimate purposes like market surveys and SEO, they also provide a cover for criminal activities, making it difficult to trace malicious traffic back to its source.
A comprehensive research project, initiated in January 2021, uncovered the extensive infrastructure of the 911.re network.
The research revealed that 911. operates without vetting or verification, allowing anyone to rent residential nodes.
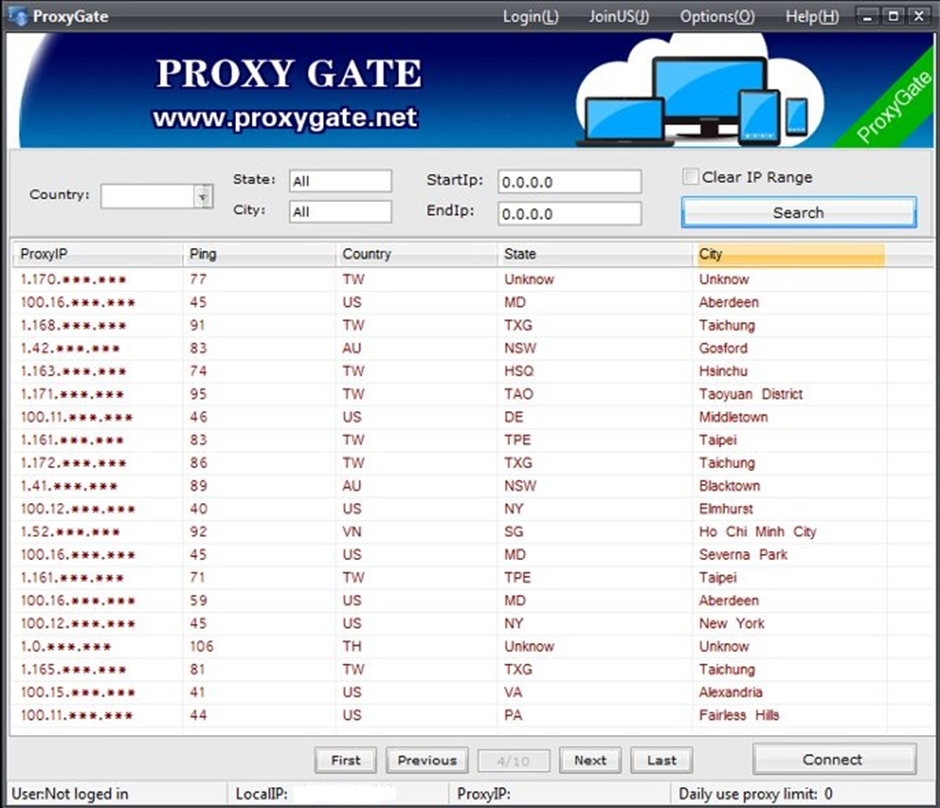
The network comprises over 120,000 residential proxy nodes distributed globally, with significant concentrations in the United States, South Korea, Peru, and Japan.
The 911.re network recruits residential nodes through two free VPN services, Mask VPN and Dew VPN.
These applications, which appear legitimate, install software on users’ computers that connect them to the 911.re network without their informed consent.
The infected nodes maintain a persistent TCP connection to command-and-control (C2) servers, making them available for use by 911.re clients.
The research highlighted several vulnerabilities and potential exploits associated with the 911.re network.
These include:
- IP Filtering-Based Service Exploits: 911. re-users can access ISP customer services and potentially gain confidential information by masquerading as the residential proxy owner.
- Lateral Movement Attacks: The infection allows 911.re users to access shared resources on the local network and probe the LAN network of the infected node.
- DNS Router Cache Poisoning: Attackers can poison the DNS cache of the LAN router, enabling further attacks.
The operation of the 911.re network raises significant legal and ethical concerns.
Residential node owners, often unaware of their participation, could face criminal or civil liability if their computers are used for malicious activities.
The lack of informed consent and the potential for severe legal consequences underscore the need for stricter regulations and oversight of such services.
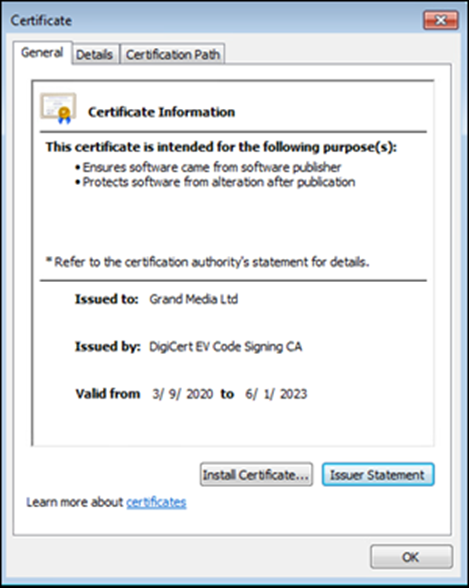
In response to these findings, the U.S. government has imposed sanctions on the entities behind the 911.re network.
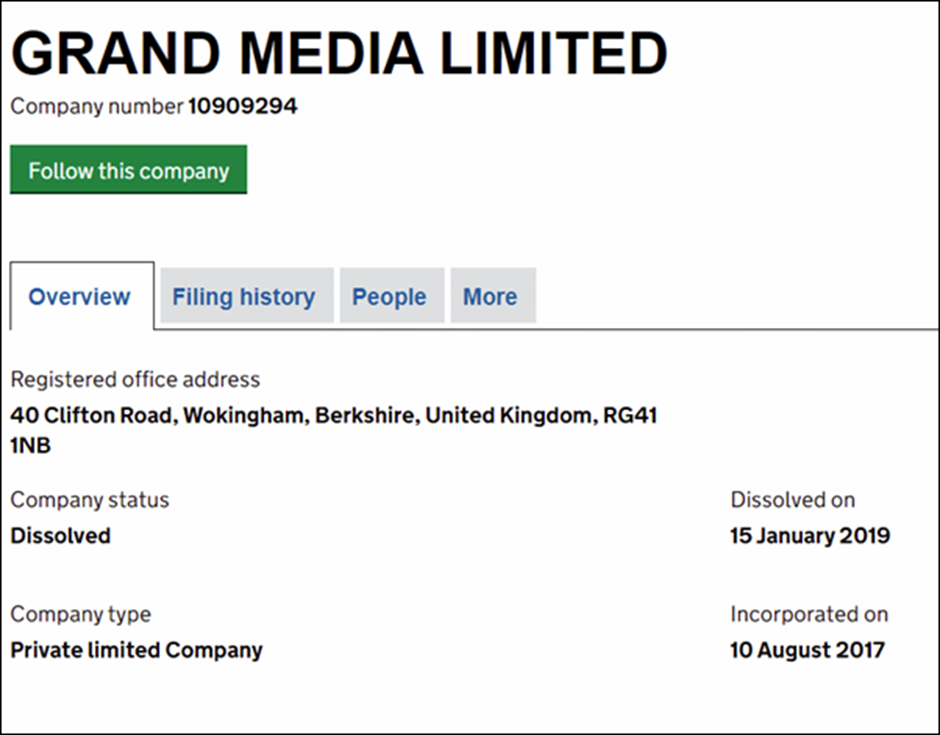
The sanctions target the shell corporations International Media Ltd and Grand Media Ltd, which are used to sign the binaries for Mask VPN and Dew VPN.
These measures aim to disrupt the operations of the 911.re network and hold its operators accountable for their role in facilitating cybercrime.

The discovery and exposure of the 911.re network highlights the growing threat of residential proxy botnets in the cybercrime landscape.
The U.S. sanctions represent a crucial step in combating this threat and protecting individuals and organizations from the risks associated with such services.
Further research and international cooperation are essential to address the network’s full extent and prevent future similar threats.
Indicators of compromise (IOCs)
Binaries
·Maskvpn.exe (2/68 virus total)
MD5: a220528f31dceddc955b791b13ac4989
SHA-1: 57a83b83a11b6e27c9e88a7835d8a84744d79bdd
SHA-256: e801fa187027537337d8b4e4bde3a7da95499172f6b1477830a216d0a385518b
·Dewvpn.exe (1/67 virus total)
MD5: 12059484a8951a8356c60c46f659a35e
SHA1: 3916aeaa61a6e97d6c1746b18c05fd77584de5d8
SHA256: daa21c58a1ace38d1eebcda6fef3502fa3492ccf09fbccfa6ce103c9222d9afc
·maskvpn-setup.exe (2/68 virus total)
MD5: f9634d85ca0138cfddfe6e58fa1c6160
SHA1: 5ffa0b96b7257d804beddb87b0a21e871a1296b4
SHA256: 1013eb0e3dbbc16c8b6d0659cca46a084e767b2d9bb8e498e07016bfdb978780
·mask_svc.exe (1/67 virus total)
MD5: c6b1934d3e588271f27a38bfeed42abb
SHA1:08072ecb9042e6f7383d118c78d45b42a418864f
SHA256: 35ec7f4d10493f28d582440719e6f622d9a2a102e40a0bc7c4924a3635a7f5a8
DewVPN-Setup.exe (1/67 virus total)
MD5: 8e8b072c93246808a7f24554ca593c59
SHA1: d06418cacd11e25af37a41724d55dffc24d6fe5b
SHA256: f422a38d72785c402948c94ae81336383a9fd48167272f29cdc434ce7e51e02b
dew_svc.exe (0/69 virus total)
MD5: 5feb35a7186a5be50b7aa158866b8aa3
SHA1:c0c7e272f3e48d8dfe559aa5f63ad3a46c76fb9e
SHA256: a8e72d202f9a83e6bdfd03a822fae6d4ee2d4b35a6f73a06e9d59e2e49b3070aDNS queries:
. vpn[.]maskvpn[.]org
· user[.]maskvpn[.]org
· net[.]dewvpn[.]com
· wan[.]dewvpn[.]net
· connect[.]dewvpn[.]ccIPv4:
98.126.176.51
· 98.126.176.52
· 98.126.176.53
· 67.198.169.2
· 98.126.244.26
· 98.126.13.146
· 174.139.80.66
· 67.229.60.114
· 174.139.78.106
· 98.126.1.130
· 174.139.100.202
· 67.198.134.186
· 98.126.5.106
Outgoing TCP ports used by Mask VPN and Dew VPN to initiate persistent C2 communications
· 441 TCP
· 430 TCP
· 433 TCP
· 434 TCP
· 436 TCP
· 440 TCP
· 439 TCP
· 435 TCP
· 428 TCP
· 432 TCP
· 438 TCPGet special offers from ANY.RUN Sandbox. Until May 31, get 6 months of free service or extra licenses. Sign up for free.
