Multiple Ukrainian hacktivist groups have launched an extensive spearphishing campaign targeting Russia’s critical aerospace and defence industries, according to a new threat intelligence report by Intrinsec.
The coordinated attacks between June and September 2025 represent an escalating cyber warfare strategy aimed at disrupting Russian military capabilities and civilian aviation operations.
The campaign involves several prominent Ukraine-aligned intrusion sets, including Head Mare, Hive0117, and the newly identified Cavalry Werewolf group, all employing sophisticated tactics to compromise sanctioned Russian entities directly supporting Moscow’s military operations.
These hackers are leveraging compromised Russian company email servers to send highly targeted spear phishing emails containing malicious attachments and credential-theft pages hosted on legitimate cloud infrastructure platforms, including IPFS, Vercel, Cloudflare, and Contabo storage buckets.
High-profile victims have already suffered significant breaches.
In July 2025, pro-Ukrainian hackers claimed responsibility for a massive attack on Aeroflot, Russia’s flagship airline, in which approximately 7,000 servers were wiped and 20 terabytes of data stolen, forcing the carrier to cancel over 50 round-trip flights.
Cyber Offensive Escalates Amid Ongoing Conflict
Days later in September, both Pulkovo Airport in Saint Petersburg and regional carrier KrasAvia experienced coordinated attacks that disrupted passenger services and forced carriers to revert to manual operations.
The same phishing template was sent on the same day through a different email
address. But this time, the link would redirect to a Vercel hosted page.
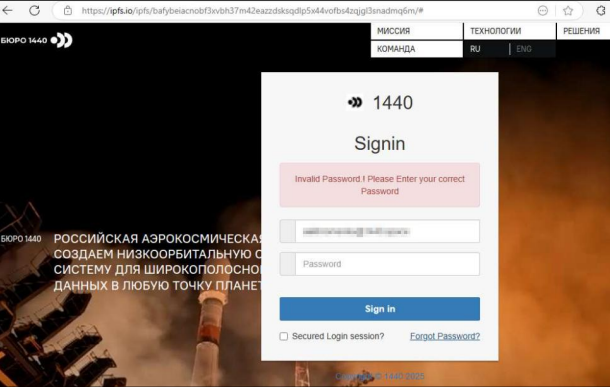
The geographic and sectoral scope of targeting is strategic. Victims include Dinamika-Avia, which provides simulators and training software for Russian fighter jets and drones; Bureau 1440, a satellite communications company providing internet connectivity for Russian railways and aircraft.
Rostvertol, a helicopter manufacturer producing the Mi-series aircraft used by Russian Armed Forces; and Kvant JSC, which manufactures electronic warfare systems including the Krasukha-4 and Rtut-BM systems actively deployed in Ukraine.
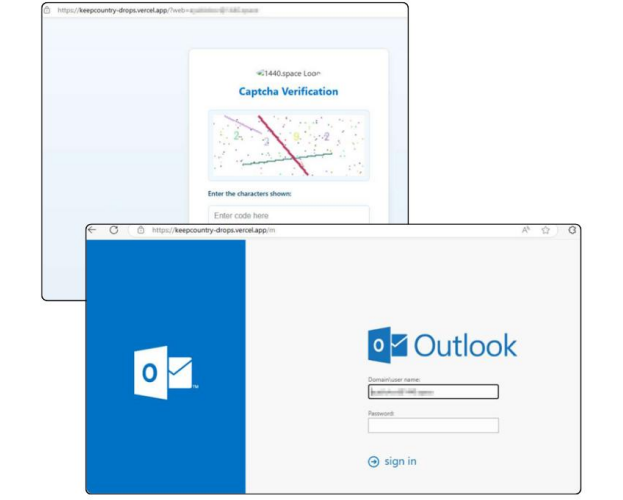
spearphishing email.
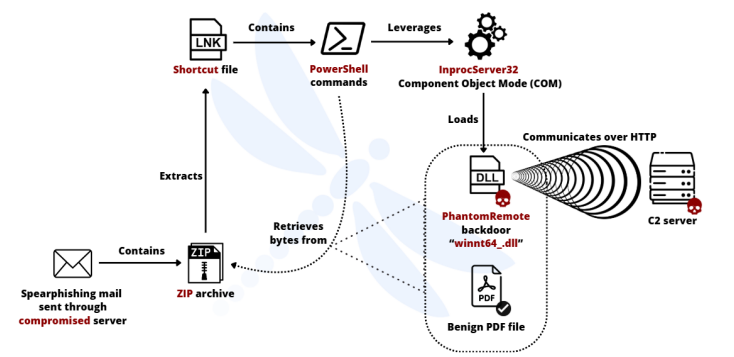
The technical sophistication of these operations varies significantly. While some campaigns deploy custom-made malware families such as PhantomRemote and DarkWatchman through multi-staged kill chains, others rely on simpler phishing pages designed to capture credentials.
Head Mare notably continues using compromised Russian company email servers as launch points, creating a challenging attribution and defence scenario.
The attackers employ credential phishing pages that mimic legitimate company login portals, hosted on legitimately-owned infrastructure to evade corporate network protections that struggle to block entire domains containing authorized content.
Implications for Regional and Global Security
The timing and coordination of these attacks suggest more than opportunistic hacktivism.
Regarding the targets of this campaign, we were able to identify three of them: Rostvert,
KORSAR, and RN-MORSKOY (Rosneft).
Intrinsec assessed with high confidence that multiple intrusion sets are operating with Ukrainian alignment, potentially with tolerance or indirect cooperation from Ukrainian intelligence agencies including the military intelligence directorate GUR and defense intelligence.
Organizations maintaining connections with Russian defence contractors are urged to implement multi-factor authentication, advanced email security gateways, enhanced employee security awareness training, and continuous network monitoring to identify unauthorized outbound connections to command-and-control servers associated with these campaigns.
Most targeted companies are already under Western sanctions for materially supporting Russia’s military operations, making them strategic pressure points in the broader cyber dimension of the Ukraine conflict.
Security experts warn that successful compromises of Russia’s aerospace sector could severely degrade both civil aviation capabilities and military efficiency.
The industry directly fuels Russian military operations by maintaining aircraft, drone, and missile production and maintenance pipelines essential for long-range strikes and sustained warfare.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
