Author: Cybernoz
Resilient Cybersecurity touches on nearly every major function of enterprise cybersecurity, from threat detection and identity management to vendor risk…
Apple released security updates to fix multiple flaws in iOS and macOS Pierluigi Paganini May 13, 2025 Apple released security…
Only 3% of organisations in Australia have achieved a mature level of readiness required to effectively withstand today’s cybersecurity threats,…
Apple released critical security updates for macOS Sequoia 15.5 on May 12, 2025, addressing over 40 vulnerabilities across system components…
Traditional vulnerability and application security tools are failing in cloud-native environments. It’s not that these tools aren’t good at what…
All organizations erect silos – silos between groups and departments, across functions and among technologies. Silos represent differences in practices,…
The rapid escalation of Common Vulnerabilities and Exposures (CVEs) has become a critical concern for security teams. Five years ago,…
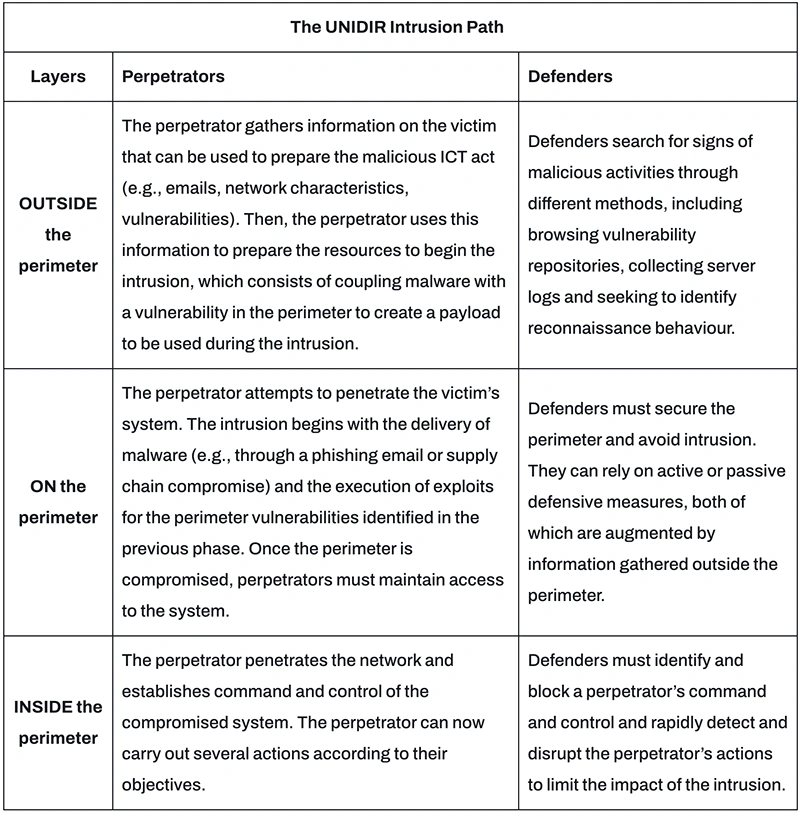
Malicious activity in the ICT environment is growing. However, a non-technical audience often struggle to understand these threats, either because…
OpenText has released its intermedium report, Retiring Legacy Applications and Databases: Proven Strategies for Government Agencies. The report provides clear…
Optimizing your online productivity is more important than ever. Whether you’re a business owner, freelancer, or simply someone looking to…
The Australian Computer Society (ACS), the professional association for Australia’s technology sector, welcomes the announcement of Prime Minister Albanese’s new…
Roblox hit with class action over alleged secret tracking of kids’ data; lawsuit claims privacy law violations and unauthorized data…