Category: Mix
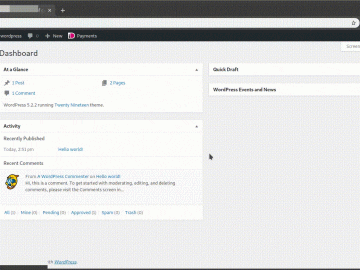
Proof of concept BackgroundWith a 60% market share WordPress is the most used CMS at this moment. Out of the…
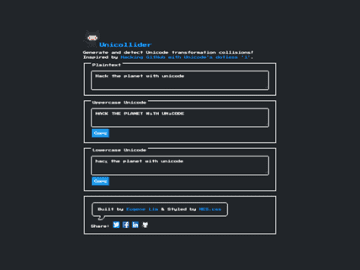
Plus a tool and tips for defenders. In this article, I will describe how Unicode — the encoding standard behind…
Hello Everybody, Welcome to my FIRST writeup! Just to give you some background, My name is Daniel, I started hacking…
This week wasn’t about me. I and millions of others were focused on the murder of George Floyd. Black Lives Matter. My progress…
Capture the flag events are particular fun events done to challenge people and get people to really think about the…
Easy Bugs for Hard Cash Continue reading on Medium » Source link
Q: How to write a BUG BOUNTY report that actually gets paid? Source link
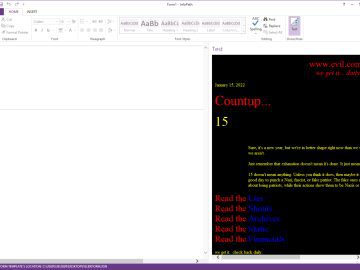
While browsing a SharePoint instance recently, I came across an interesting URL in the form https:///_layouts/FormServer.aspx?XsnLocation=https:///resource/Forms/template.xsn. The page itself displayed…
This year I released a challenge for the Full Stack Web Attack class: Whilst several people had solved the challenge,…
When Assetnote Continuous Security (CS) monitors your attack surface, one of the things it looks for are instances of WebPageTest….
This writeup walks you through the full process as to how I found a pretty bad Insecure Direct Object Reference…
After a long day of trying and failing to find vulnerabilities on the Verizon Media bug bounty program I decided…